Question 161
Refer to the following code:
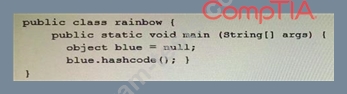
Which of the following vulnerabilities would occur if this is executed?

Which of the following vulnerabilities would occur if this is executed?
Question 162
The Chief Information Officer (CIO) has heard concerns from the business and the help desk about frequent user account lockouts Which of the following account management practices should be modified to ease the burden?
Question 163
A system administrator is reviewing the following information from a compromised server.

Given the above information, which of the following processes was MOST likely exploited via remote buffer overflow attack?

Given the above information, which of the following processes was MOST likely exploited via remote buffer overflow attack?
Question 164
A security operation team recently detected a breach of credentials. The team mitigated the risk and followed proper processes to reduce risk. Which of the following processes would BEST help prevent this issue from happening again?
Question 165
Joe, an employee, asks a coworker how long ago Ann started working at the help desk. The coworker expresses surprise since nobody named Ann works at the help desk. Joe mentions that Ann called several people in the customer service department 10 help reset their passwords over the phone due to unspecied
"server issues.' Which of the following has occurred?
"server issues.' Which of the following has occurred?

