Question 151
A software development company needs to augment staff by hiring consultants for a high-stakes project The project has the following requirements:
* Consultants will have access to flighty confidential, proprietary data.
* Consultants will not be provided with company-owned assets.
* Work needs to start Immediately.
* Consultants will be provided with Internal email addresses for communications.
Which of the following solutions is the BEST method lor controlling data exfiltration during this project?
* Consultants will have access to flighty confidential, proprietary data.
* Consultants will not be provided with company-owned assets.
* Work needs to start Immediately.
* Consultants will be provided with Internal email addresses for communications.
Which of the following solutions is the BEST method lor controlling data exfiltration during this project?
Question 152
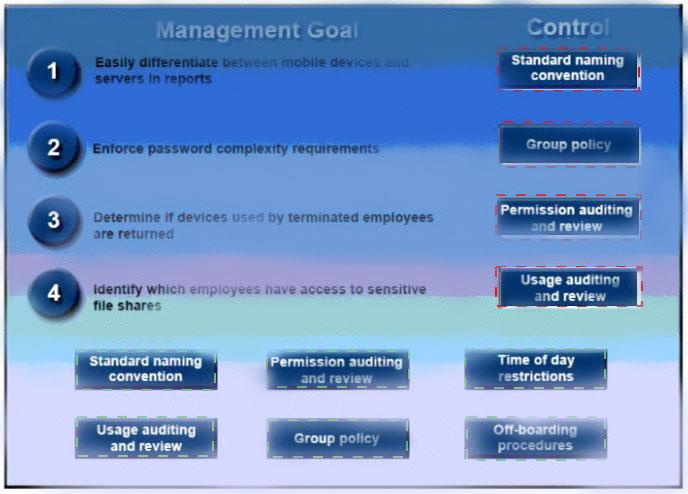
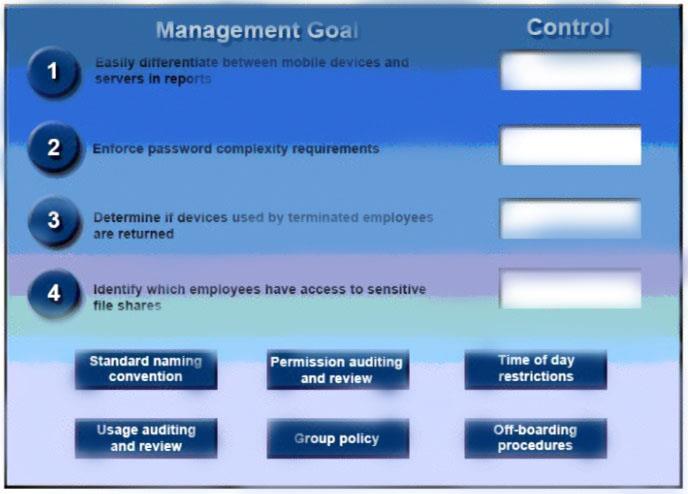
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the appropriate control used to accomplish the account management goal. Options may be used once or not at all.

Question 153
A system administrator must configure the company's authentication system to ensure that users will be unable to reuse the last ten passwords within a six months period. Which of the following settings must be configured? (Select Two)
Question 154
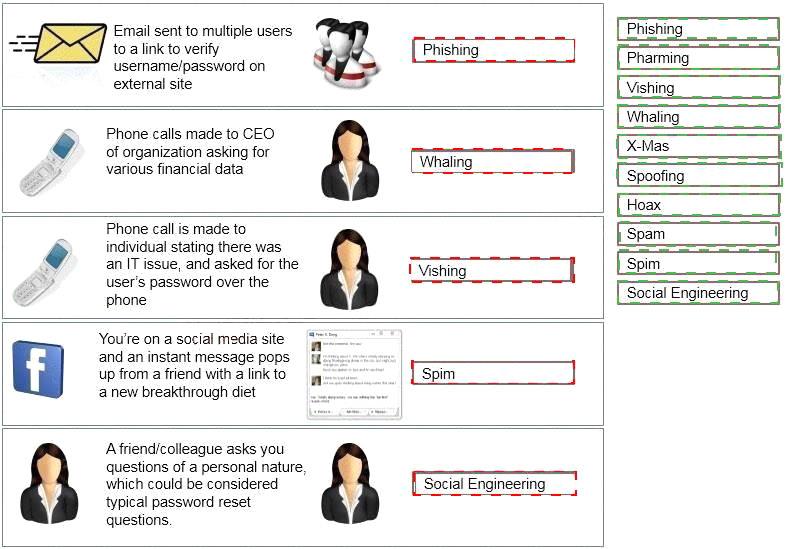
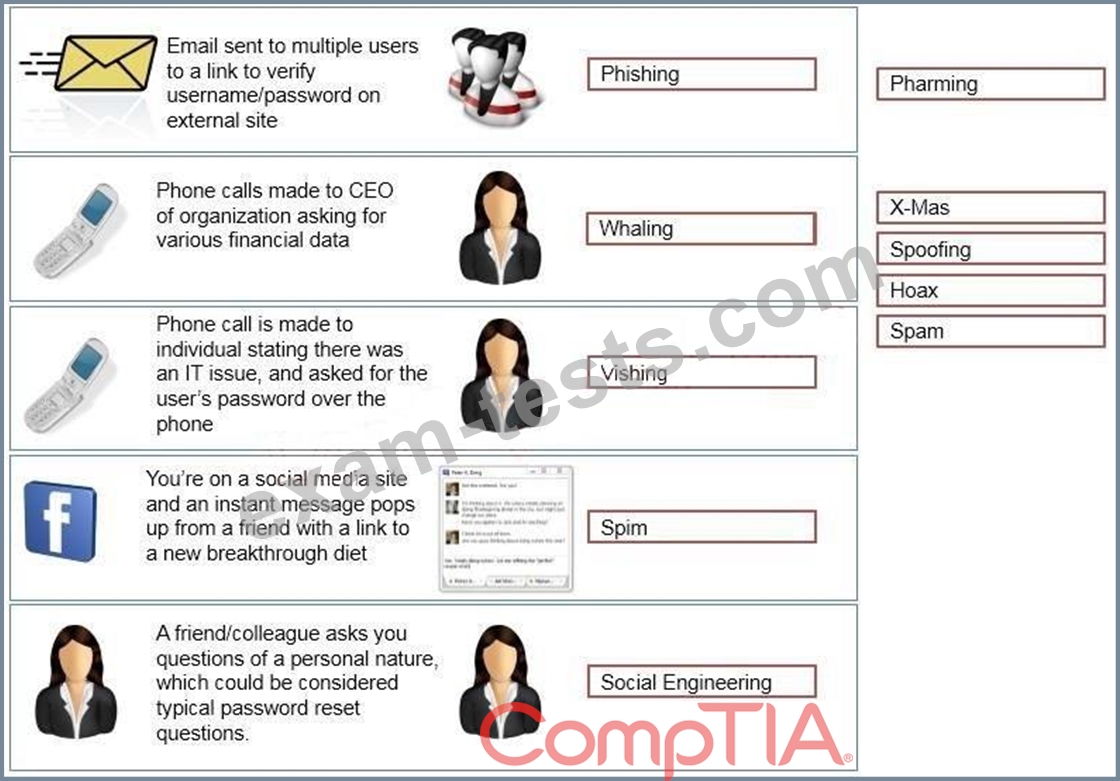
Task: Determine the types of attacks below by selecting an option from the dropdown list.
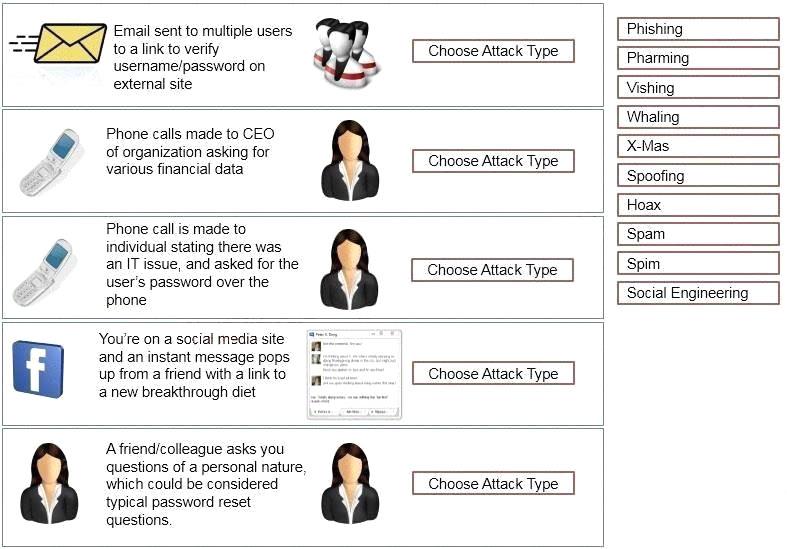

Question 155
Which of the following BEST describes an important security advantage yielded by implementing vendor diversity?