Question 266
Refer to the following code:

Which of the following vulnerabilities would occur if this is executed?

Which of the following vulnerabilities would occur if this is executed?
Question 267
A Chief Information Security Officer (CISO) has instructed the information assurance staff to act upon a fast- spreading virus.
Which of the following steps in the incident response process should be taken NEXT?
Which of the following steps in the incident response process should be taken NEXT?
Question 268
An organization identifies a number of hosts making outbound connections to a known malicious IP over port TCP 80. The organization wants to identify the data being transmitted and prevent future connections to this IP. Which of the following should the organization do to achieve this outcome?
Question 269
Poor inventory control practices can lead to undetected and potentially catastrophic system exploitation due to:
Question 270
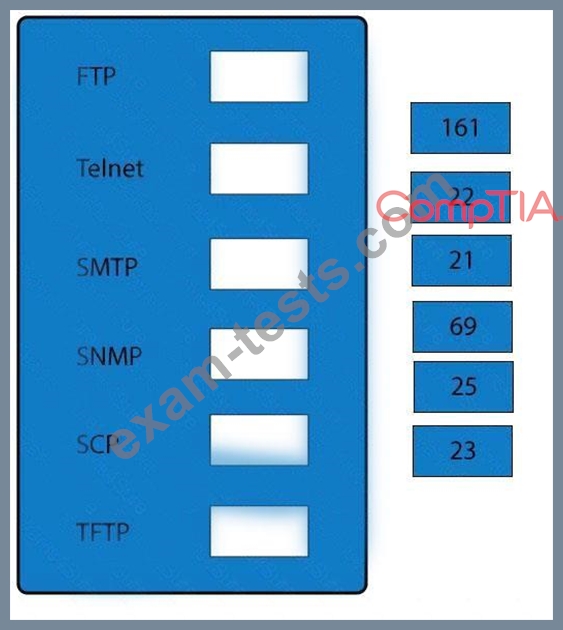
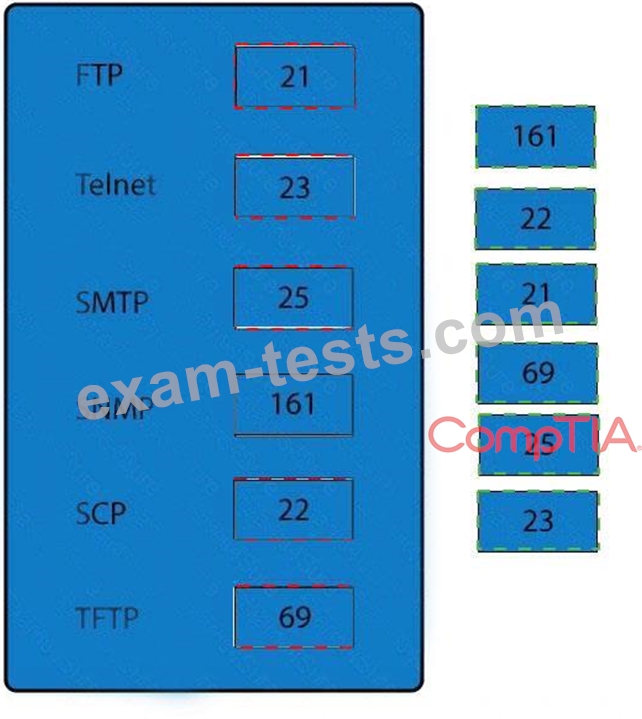
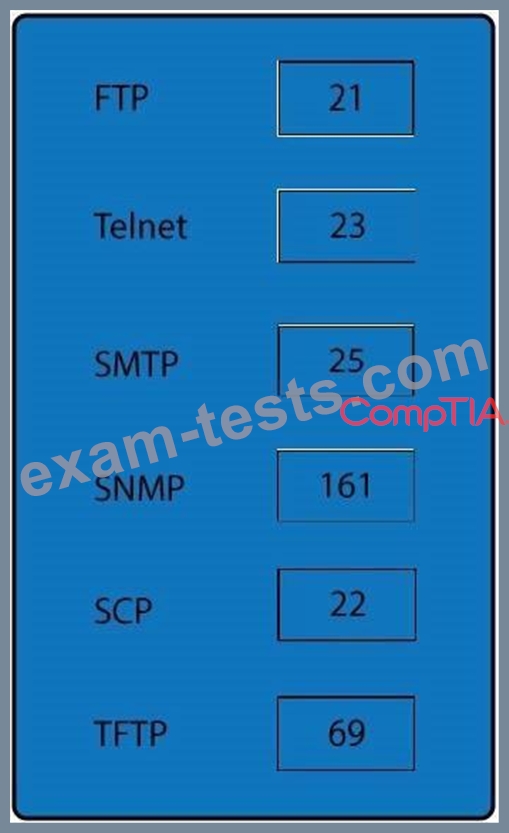
Drag and drop the correct protocol to its default port.