Question 271
A Security analyst is diagnosing an incident in which a system was compromised from an external IP address. The socket identified on the firewall was traced to 207.46.130.6666. Which of the following should the security analyst do to determine if the compromised system still has an active connection?
Question 272
An application developer is designing an application involving secure transports from one service to another that will pass over port 80 for a request.
Which of the following secure protocols is the developer MOST likely to use?
Which of the following secure protocols is the developer MOST likely to use?
Question 273
A security analyst observes the following events in the logs of an employee workstation:
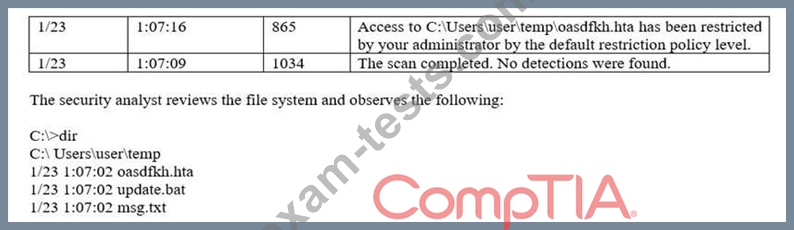
Given the information provided, which of the following MOST likely occurred on the workstation?

Given the information provided, which of the following MOST likely occurred on the workstation?
Question 274
Which of the following technologies employ the use of SAML? (Select TWO).
Question 275
A penetration tester harvests potential usernames from a social networking site. The penetration tester
then uses social engineering to attempt to obtain associated passwords to gain unauthorized access to
shares on a network server.
Which of the following methods is the penetration tester MOST likely using?
then uses social engineering to attempt to obtain associated passwords to gain unauthorized access to
shares on a network server.
Which of the following methods is the penetration tester MOST likely using?

