Question 291
Ann is the IS manager for several new systems in which the classification of the systems' data are being decided. She is trying to determine the sensitivity level of the data being processed.
Which of the following people should she consult to determine the data classification?
Which of the following people should she consult to determine the data classification?
Question 292
A company needs to implement an on-premises system that allows partner organizations to exchange order and inventory data electronically with the company over the Internet. The security architect must ensure the data is protected while minimizing the overhead associated with managing individual partner connections. Which of the following should the security architect recommend?
Question 293
A security analyst is investigating a suspected security breach and discovers the following in the logs of the potentially compromised server:
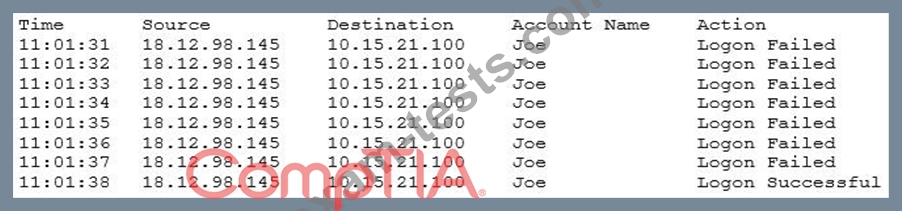
Which of the following would be the BEST method for preventing this type of suspected attack in the future?

Which of the following would be the BEST method for preventing this type of suspected attack in the future?
Question 294
An incident responder receives a call from a user who reports a computer is exhibiting symptoms consistent with a malware infection.
Which of the following steps should the responder perform NEXT?
Which of the following steps should the responder perform NEXT?
Question 295
Legal authorities notify a company that its network has been compromised for the second time in two years.
The investigation shows the attackers were able to use the same vulnerability on different systems in both attacks.
Which of the following would have allowed the security team to use historical information to protect against the second attack?
The investigation shows the attackers were able to use the same vulnerability on different systems in both attacks.
Which of the following would have allowed the security team to use historical information to protect against the second attack?

