Question 301
A technician receives a device with the following anomalies:
Frequent pop-up ads
Show response-time switching between active programs Unresponsive peripherals The technician reviews the following log file entries:
File Name Source MD5 Target MD5
Status
antivirus.exe F794F21CD33E4F57890DDEA5CF267ED2 F794F21CD33E4F57890DDEA5CF267ED2 Automatic iexplore.exe 7FAAF21CD33E4F57890DDEA5CF29CCEA AA87F21CD33E4F57890DDEAEE2197333 Automatic service.exe 77FF390CD33E4F57890DDEA5CF28881F
77FF390CD33E4F57890DDEA5CF28881F Manual USB.exe E289F21CD33E4F57890DDEA5CF28EDC0 E289F21CD33E4F57890DDEA5CF28EDC0 Stopped Based on the above output, which of the following should be reviewed?
Frequent pop-up ads
Show response-time switching between active programs Unresponsive peripherals The technician reviews the following log file entries:
File Name Source MD5 Target MD5
Status
antivirus.exe F794F21CD33E4F57890DDEA5CF267ED2 F794F21CD33E4F57890DDEA5CF267ED2 Automatic iexplore.exe 7FAAF21CD33E4F57890DDEA5CF29CCEA AA87F21CD33E4F57890DDEAEE2197333 Automatic service.exe 77FF390CD33E4F57890DDEA5CF28881F
77FF390CD33E4F57890DDEA5CF28881F Manual USB.exe E289F21CD33E4F57890DDEA5CF28EDC0 E289F21CD33E4F57890DDEA5CF28EDC0 Stopped Based on the above output, which of the following should be reviewed?
Question 302
A consultant has been tasked to assess a client's network. The client reports frequent network outages.
Upon viewing the spanning tree configuration, the consultant notices that an old and law performing edge switch on the network has been elected to be the root bridge.
Which of the following explains this scenario?
Upon viewing the spanning tree configuration, the consultant notices that an old and law performing edge switch on the network has been elected to be the root bridge.
Which of the following explains this scenario?
Question 303
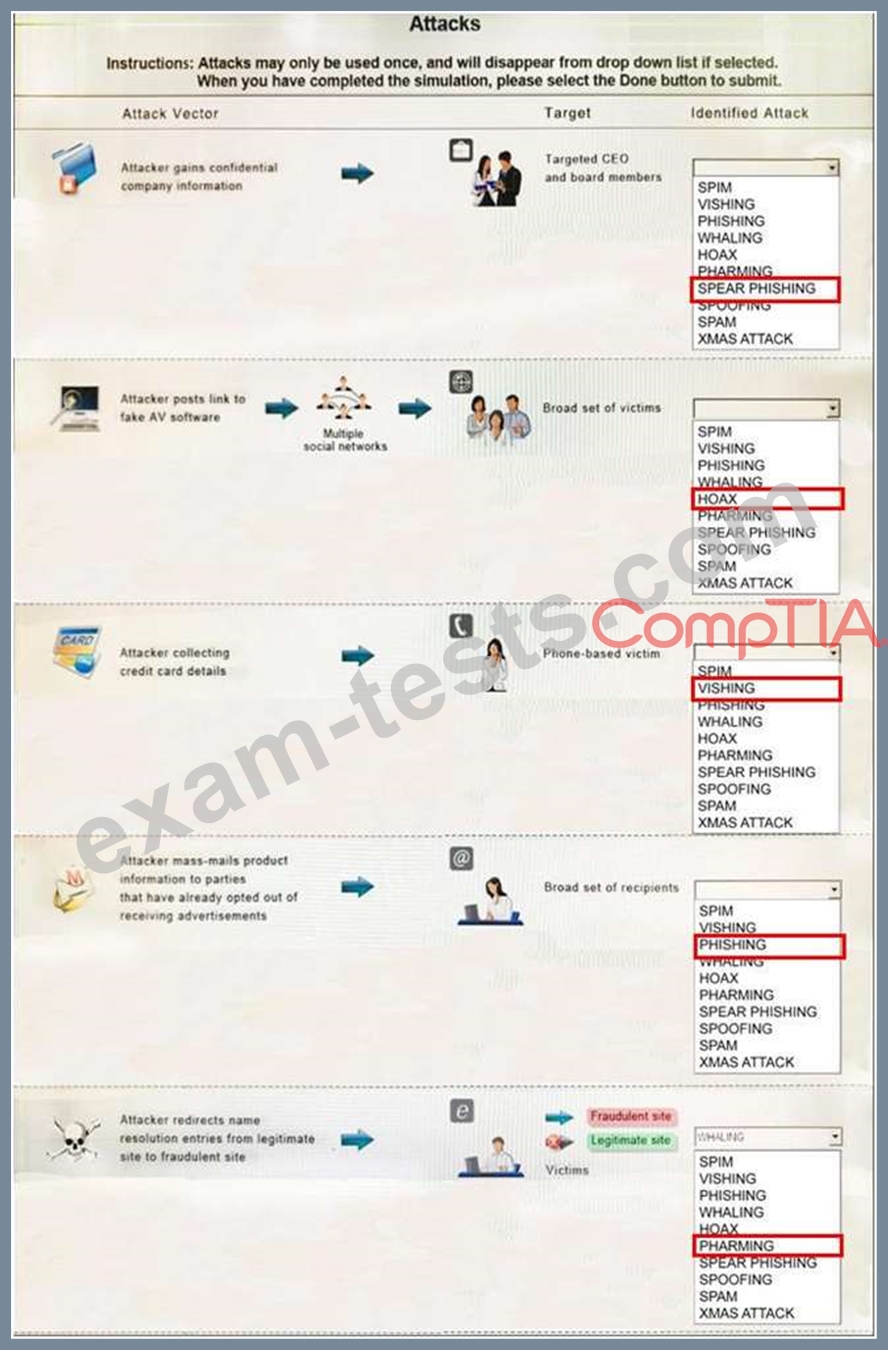
Select the appropriate attack from each drop down list to label the corresponding illustrated attack.
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.
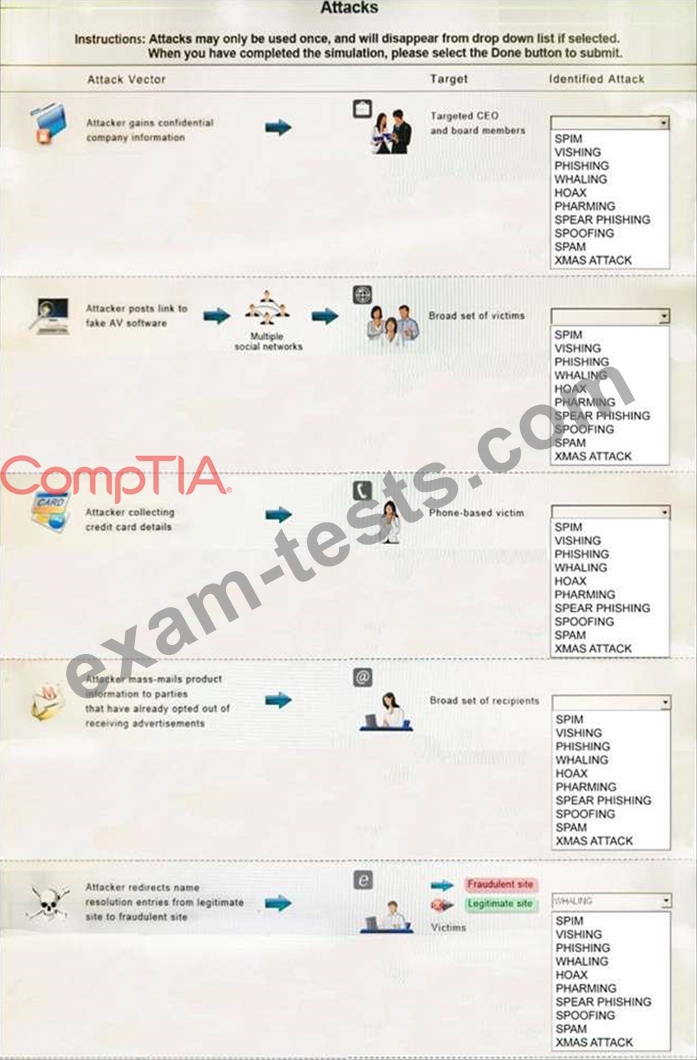
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.

Question 304
A security administrator is analyzing a user report in which the computer exhibits odd network-related outages.
The administrator, however, does not see any suspicious processes running. A prior technician's notes indicate the machine has been remediated twice, but the system still exhibits odd behavior. Files were deleted from the system recently.
Which of the following is the MOST likely cause of this behavior?
The administrator, however, does not see any suspicious processes running. A prior technician's notes indicate the machine has been remediated twice, but the system still exhibits odd behavior. Files were deleted from the system recently.
Which of the following is the MOST likely cause of this behavior?
Question 305
Task: Configure the firewall (fill out the table) to allow these four rules:
* Only allow the Accounting computer to have HTTPS access to the Administrative server.
* Only allow the HR computer to be able to communicate with the Server 2 System over SCP.
* Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2
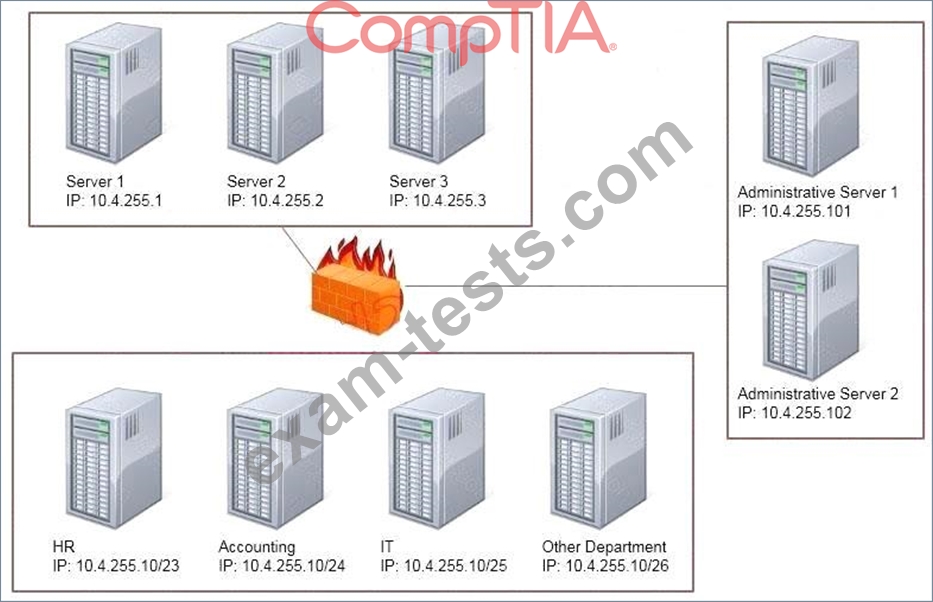
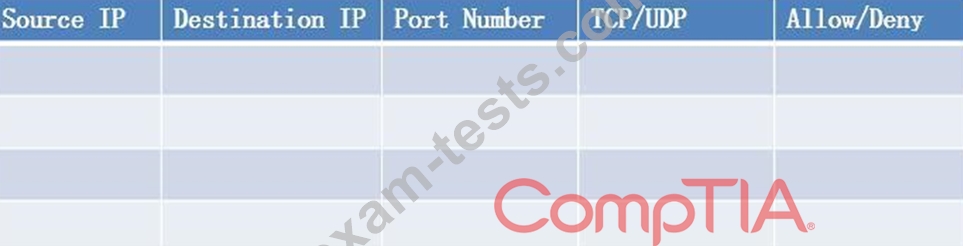
* Only allow the Accounting computer to have HTTPS access to the Administrative server.
* Only allow the HR computer to be able to communicate with the Server 2 System over SCP.
* Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2