Question 296
A security engineer must install the same x.509 certificate on three different servers. The client application that connects to the server performs a check to ensure the certificate matches the host name. Which of the following should the security engineer use?
Question 297
An analyst generates the following color-coded table shown in the exhibit to help explain the risk of potential incidents in the company. The vertical axis indicates the likelihood or an incident, while the horizontal axis indicates the impact.
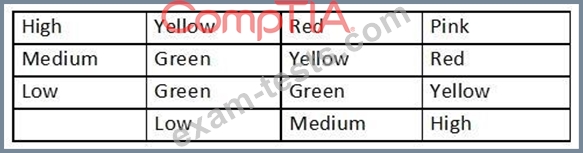
Which of the following is this table an example of?

Which of the following is this table an example of?
Question 298
An organization's internal auditor discovers that large sums of money have recently been paid to a vendor that management does not recognize. The IT security department is asked to investigate the organizations the organization's ERP system to determine how the accounts payable module has been used to make these vendor payments.
The IT security department finds the following security configuration for the accounts payable module:
New Vendor Entry - Required Role: Accounts Payable Clerk

New Vendor Approval - Required Role: Accounts Payable Clerk

Vendor Payment Entry - Required Role: Accounts Payable Clerk

Vendor Payment Approval - Required Role: Accounts Payable Manager

Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk?
A:

B:

C:

D:

The IT security department finds the following security configuration for the accounts payable module:
New Vendor Entry - Required Role: Accounts Payable Clerk

New Vendor Approval - Required Role: Accounts Payable Clerk

Vendor Payment Entry - Required Role: Accounts Payable Clerk

Vendor Payment Approval - Required Role: Accounts Payable Manager

Which of the following changes to the security configuration of the accounts payable module would BEST mitigate the risk?
A:

B:

C:

D:

Question 299
An administrator is configuring access to information located on a network file server named
"Bowman." The files are located in a folder name "BalkFiles." The files are only for use by the
"Matthews" division and should be read-only. The security policy requires permissions for shares to be managed at the file system later and also requires those permissions to be set according to a least privilege model. Security policy for this data type also dictates that administrator-level accounts on the system have full access to the files.
The administrator configures the file share according to the following table:
Share permissions
1 Everyone Full control
File System permissions
2 Bowman\Users Modify Inherited
3 Domain\Matthews Read Not inherited
4 Bowman\System Full control Inherited
5 Bowman\Administors Full control Not inherited
Which of the following rows has been misconfigured?
"Bowman." The files are located in a folder name "BalkFiles." The files are only for use by the
"Matthews" division and should be read-only. The security policy requires permissions for shares to be managed at the file system later and also requires those permissions to be set according to a least privilege model. Security policy for this data type also dictates that administrator-level accounts on the system have full access to the files.
The administrator configures the file share according to the following table:
Share permissions
1 Everyone Full control
File System permissions
2 Bowman\Users Modify Inherited
3 Domain\Matthews Read Not inherited
4 Bowman\System Full control Inherited
5 Bowman\Administors Full control Not inherited
Which of the following rows has been misconfigured?
Question 300
A user attempts to send an email to an external domain and quickly receives a bounce-back message. The user then contacts the help desk stating the message is important and needs to be delivered immediately. While digging through the email logs, a systems administrator finds the email and bounce-back details:
Your email has been rejected because It appears to contain SSN Information. Sending SSN information via email external recipients violates company policy.
Which of the following technologies successfully stopped the email from being sent?
Your email has been rejected because It appears to contain SSN Information. Sending SSN information via email external recipients violates company policy.
Which of the following technologies successfully stopped the email from being sent?

