Question 346
HOTSPOT
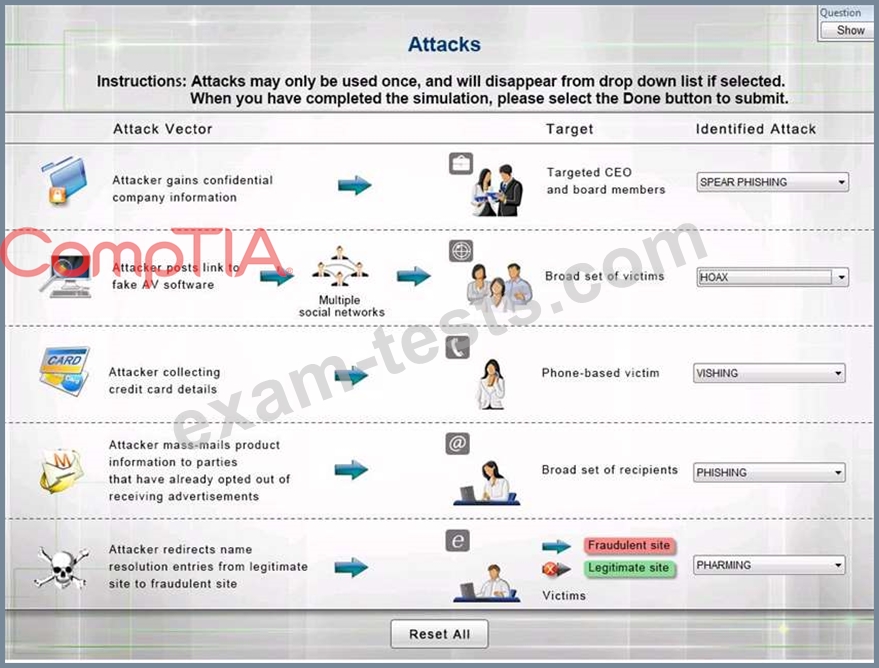
Select the appropriate attack from each drop down list to label the corresponding illustrated attack Instructions: Attacks may only be used once, and will disappear from drop down list if selected.
When you have completed the simulation, please select the Done button to submit.
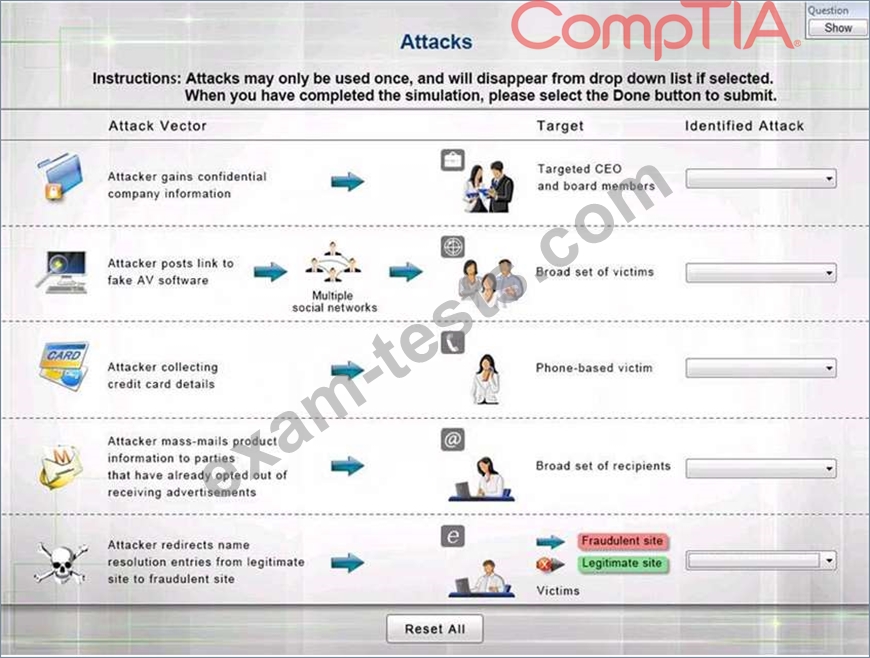
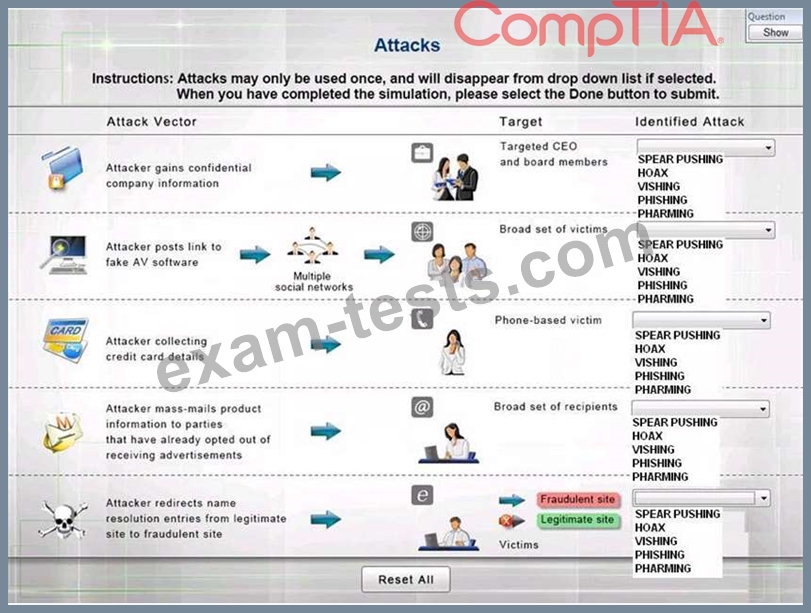
Select the appropriate attack from each drop down list to label the corresponding illustrated attack Instructions: Attacks may only be used once, and will disappear from drop down list if selected.
When you have completed the simulation, please select the Done button to submit.


Question 347
Which of the following methods minimizes the system interaction when gathering information to conduct a vulnerability assessment of a router?
Question 348
A network administrator wants to implement a method of securing internal routing. Which of the following should the administrator implement?
Question 349
A security administrator is reviewing the following network capture:

Which of the following malware is MOST likely to generate the above information?

Which of the following malware is MOST likely to generate the above information?
Question 350
Which of the following best describes the initial processing phase used in mobile device forensics?