Question 351
A security program manager wants to actively test the security posture of a system. The system is not yet in production and has no uptime requirement or active user base.
Which of the following methods will produce a report which shows vulnerabilities that were actually exploited?
Which of the following methods will produce a report which shows vulnerabilities that were actually exploited?
Question 352
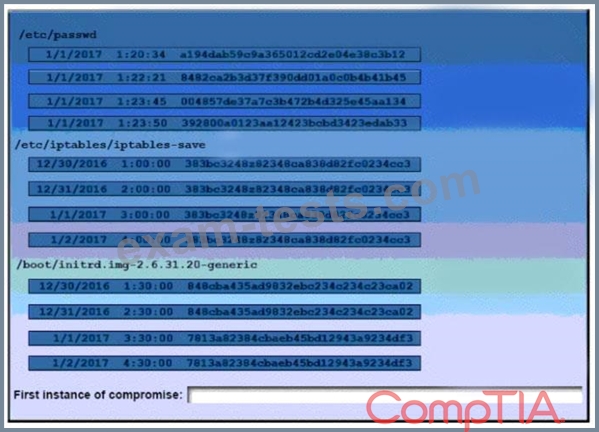
A security auditor is reviewing the following output from file integrity monitoring software installed on a very busy server at a large service provider. The server has not been updates since it was installed. Drag and drop the log entry that identifies the first instance of server compromise.

Question 353
A security administrator is configuring a RADIUS server for wireless authentication. The configuration must ensure client credentials are encrypted end-to-end between the client and the authenticator.
Which of the following protocols should be configured on the RADIUS server? (Choose two.)
Which of the following protocols should be configured on the RADIUS server? (Choose two.)
Question 354
While testing a new vulnerability scanner, a technician becomes concerned about reports that list security concerns that are not present on the systems being tested. Which of the following BEST describes this flaw?
Question 355
A user is unable to obtain an IP address from the corporate DHCP server. Which of the following is MOST likely the cause?