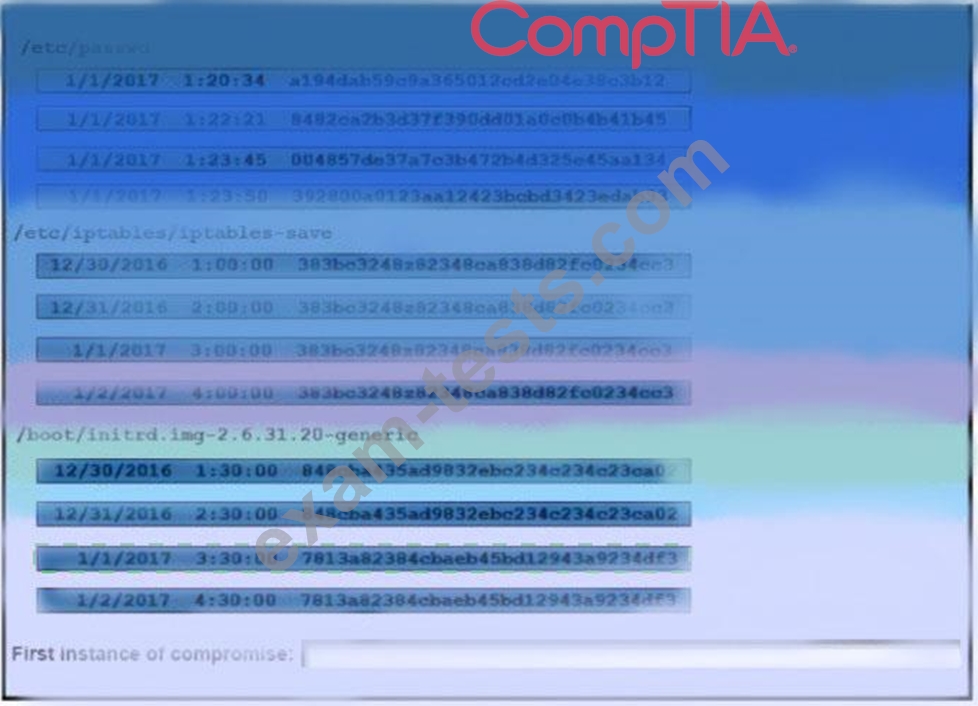
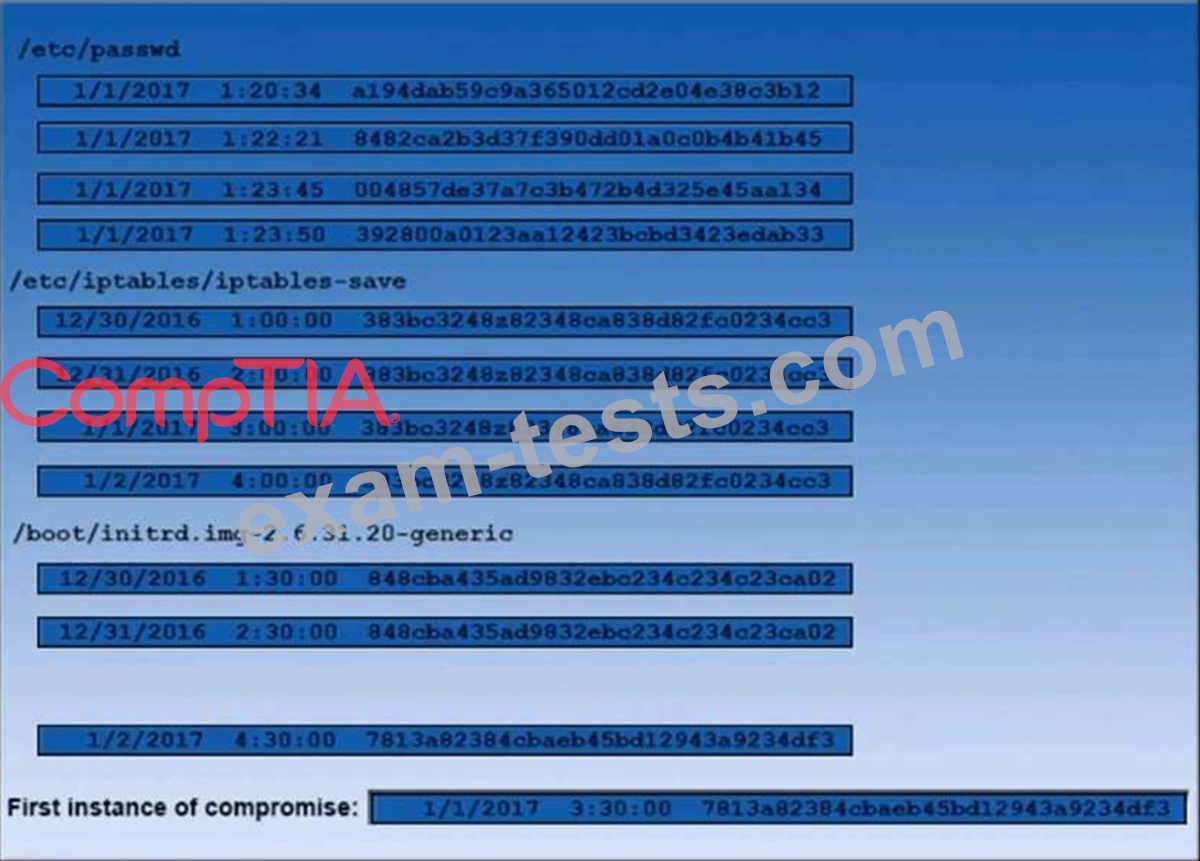
Question 361
A security auditor is reviewing the following output from file integrity monitoring software installed on a very busy server at a large service provider. The server has not been updates since it was installed. Drag and drop the log entry that identifies the first instance of server compromise.


Question 362
A technician is investigating a report of unusual behavior and slow performance on a company-owned laptop.
The technician runs a command and reviews the following information:
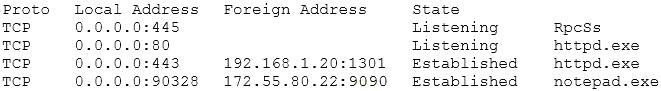
Based on the above information, which of the following types of malware should the technician report?
The technician runs a command and reviews the following information:

Based on the above information, which of the following types of malware should the technician report?
Question 363
A company is developing a new secure technology and requires computers being used for development to be isolated. Which of the following should be implemented to provide the MOST secure environment?
Question 364
A company is executing a strategy to encrypt and sign all proprietary data in transit. The company recently deployed PKI services to support this strategy.
Which of the following protocols supports the strategy and employs certificates generated by the PKI? (Choose three.)
Which of the following protocols supports the strategy and employs certificates generated by the PKI? (Choose three.)
Question 365
A company recently implemented a new security system. In the course of configuration, the security administrator adds the following entry:
#Whitelist USB\VID_13FE&PID_4127&REV_0100
Which of the following security technologies is MOST likely being configured?
#Whitelist USB\VID_13FE&PID_4127&REV_0100
Which of the following security technologies is MOST likely being configured?