Question 411
The firewall administrator is adding a new certificate for the company's remote access solution. The solution requires that the uploaded file contain the entire certificate chain for the certificate to load properly. The administrator loads the company certificate and the root CA certificate into the file. The file upload is rejected.
Which of the following is required to complete the certificate chain?
Which of the following is required to complete the certificate chain?
Question 412
An information security specialist is reviewing the following output from a Linux server.
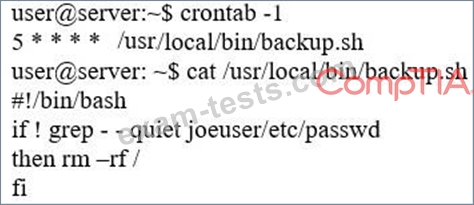
Based on the above information, which of the following types of malware was installed on the server?

Based on the above information, which of the following types of malware was installed on the server?
Question 413
A security analyst wishes to increase the security of an FTP server. Currently, all trails to the FTP server is unencrypted. Users connecting to the FTP server use a variety of modem
FTP client software. The security analyst wants to keep the same port and protocol, while also still allowing unencrypted connections. Which of the following would BEST accomplish these goals?
FTP client software. The security analyst wants to keep the same port and protocol, while also still allowing unencrypted connections. Which of the following would BEST accomplish these goals?
Question 414
An administrator intends to configure an IPSec solution that provides ESP with integrity protection, but not confidentiality protection.
Which of the following AES modes of operation would meet this integrity-only requirement?
Which of the following AES modes of operation would meet this integrity-only requirement?
Question 415
A company is planning to utilize its legacy desktop systems by converting them into dummy terminals and moving all heavy applications and storage to a centralized server that hosts all of the company's required desktop applications. Which of the following describes the BEST deployment method to meet these requirements?

