Question 386
Which of the following characteristics differentiate a rainbow table attack from a brute force attack? (Select
two.)
two.)
Question 387
An in-house penetration tester is using a packet capture device to listen in on network communications.
This is an example of:
This is an example of:
Question 388
A security administrator suspects that a DDoS attack is affecting the DNS server. The administrator accesses a workstation with the hostname of workstation01 on the network and obtains the following output from the ipconfig command:
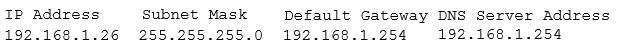
The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occuring?

The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occuring?
Question 389
A security analyst is diagnosing an incident in which a system was compromised from an external IP address. The socket identified on the firewall was traced to 207.46.130.0:6666.
Which of the following should the security analyst do to determine if the compromised system still has an active connection?
Which of the following should the security analyst do to determine if the compromised system still has an active connection?
Question 390
A security analyst is reviewing the password policy for a service account that is used for a critical network service. The password policy for this account is as follows:
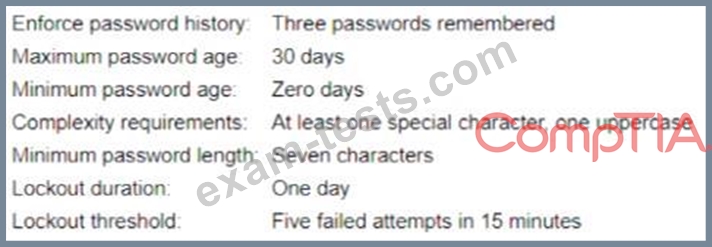
Which of the following adjustments would be the MOST appropriate for the service account?

Which of the following adjustments would be the MOST appropriate for the service account?

