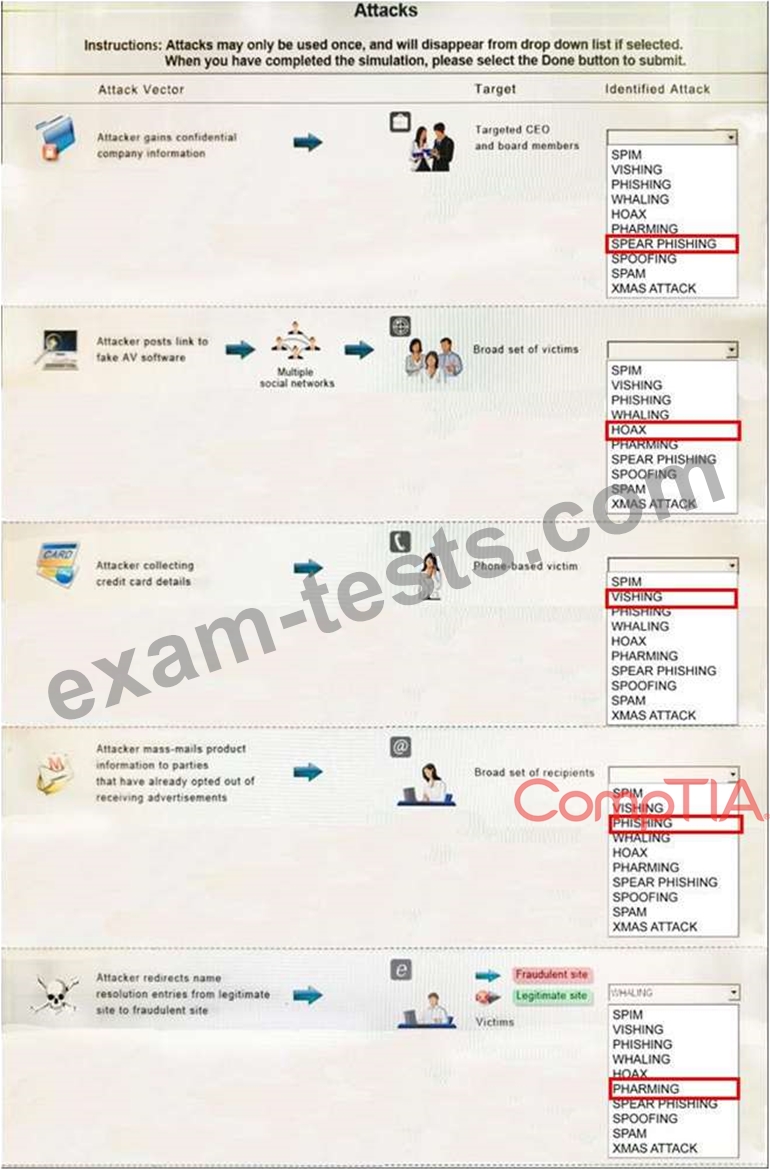
Question 431
Select the appropriate attack from each drop down list to label the corresponding illustrated attack.
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.
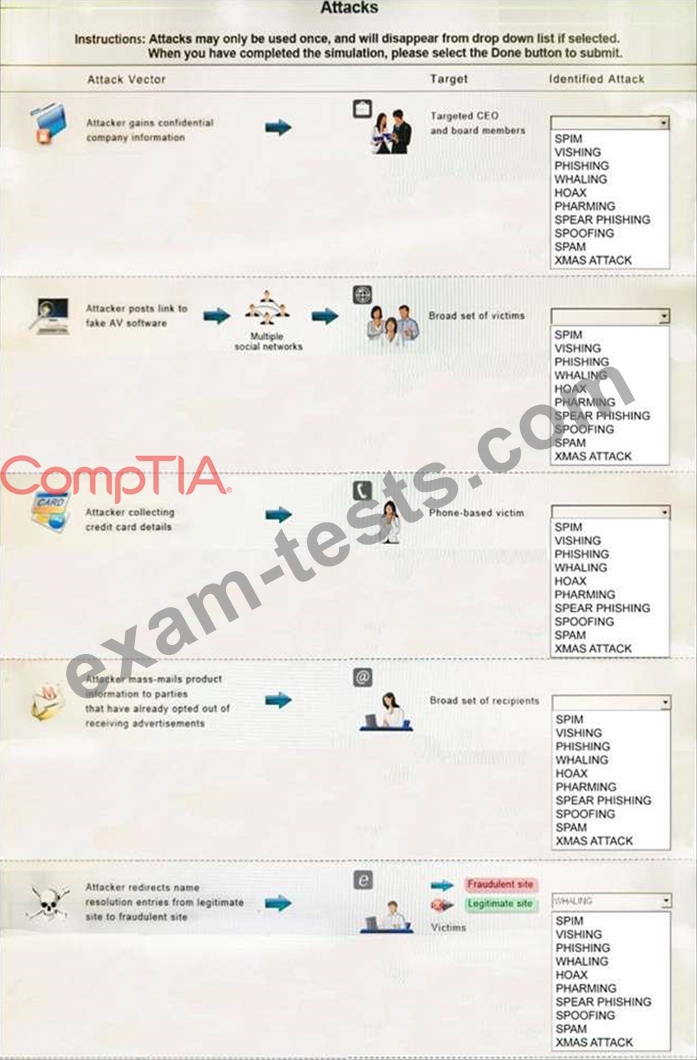
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.

Question 432
Which of the following locations contain the MOST volatile data?
Question 433
A penetration testing team deploys a specifically crafted payload to a web server, which results in opening a new session as the web server daemon. This session has full read/write access to the file system and the admin console. Which of the following BEST describes the attack?
Question 434
A user receives an email from ISP indicating malicious traffic coming from the user's home network is detected. The traffic appears to be Linux-based, and it is targeting a website that was recently featured on the news as being taken offline by an Internet attack. The only Linux device on the network is a home surveillance camera system. Which of the following BEST describes what is happening?
Question 435
An audit reported has identifies a weakness that could allow unauthorized personnel access to the facility
at its main entrance and from there gain access to the network. Which of the following would BEST resolve
the vulnerability?
at its main entrance and from there gain access to the network. Which of the following would BEST resolve
the vulnerability?