Question 246
A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
Question 247
An engineer needs to deploy a security measure to identify and prevent data tampering within the enterprise. Which of the following will accomplish this goal?
Question 248
A network administrator has been asked to install an IDS to improve the security posture of an organization.
Which of the following control types is an IDS?
Which of the following control types is an IDS?
Question 249
A network administrator needs to build out a new datacenter, with a focus on resiliency and uptime. Which of the following would BEST meet this objective? (Choose two.)
Question 250
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst MOST likely seeing?
A)
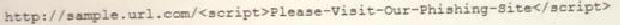
B)

C)
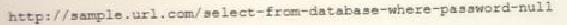
D)
A)
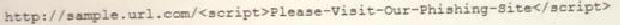
B)

C)
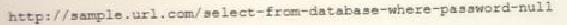
D)

