Question 256
Which of the following is a team of people dedicated to testing the effectiveness of organizational security programs by emulating the techniques of potential attackers?
Question 257
The following are the logs of a successful attack.
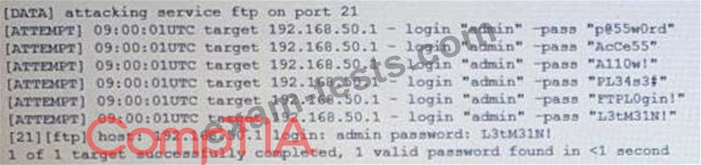
Which of the following controls would be BEST to use to prevent such a breach in the future?

Which of the following controls would be BEST to use to prevent such a breach in the future?
Question 258
A developer is building a new portal to deliver single-pane-of-glass management capabilities to customers with multiple firewalls. To Improve the user experience, the developer wants to implement an authentication and authorization standard that uses security tokens that contain assertions to pass user Information between nodes. Which of the following roles should the developer configure to meet these requirements? (Select TWO).
Question 259
An enterprise has hired an outside security firm to conduct penetration testing on its network and applications.
The firm has only been given the documentation available to the customers of the applications. Which of the following BEST represents the type of testing that will occur?
The firm has only been given the documentation available to the customers of the applications. Which of the following BEST represents the type of testing that will occur?
Question 260
Joe, an employee, receives an email stating he won the lottery. The email includes a link that requests a name, mobile phone number, address, and date of birth be provided to confirm Joe's identity before sending him the prize. Which of the following BEST describes this type of email?

