Question 251
A user recently entered a username and password into a recruiting application website that had been forged to look like the legitimate site. Upon investigation, a security analyst identifies the following:
* The legitimate website's IP address is 10.1.1.20 and eRecruit.local resolves to this IP.
* The forged website's IP address appears to be 10.2.12.99, based on NetFlow records.
* All three of the organization's DNS servers show the website correctly resolves to the legitimate IP.
* DNS query logs show one of the three DNS servers returned a result of 10.2.12.99 (cached) at the approximate time of the suspected compromise.
Which of the following MOST likely occurred?
* The legitimate website's IP address is 10.1.1.20 and eRecruit.local resolves to this IP.
* The forged website's IP address appears to be 10.2.12.99, based on NetFlow records.
* All three of the organization's DNS servers show the website correctly resolves to the legitimate IP.
* DNS query logs show one of the three DNS servers returned a result of 10.2.12.99 (cached) at the approximate time of the suspected compromise.
Which of the following MOST likely occurred?
Question 252
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
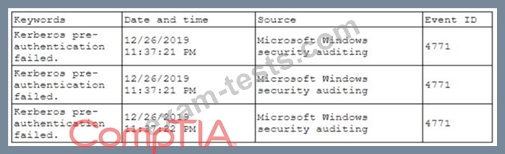
To better understand what is going on, the analyst runs a command and receives the following output:
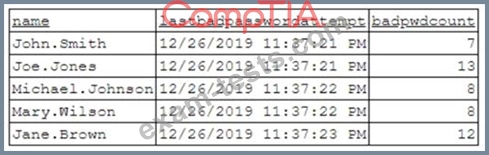
Based on the analyst's findings, which of the following attacks is being executed?

To better understand what is going on, the analyst runs a command and receives the following output:

Based on the analyst's findings, which of the following attacks is being executed?
Question 253
Which of the following is the MOST secure but LEAST expensive data destruction method for data that is stored on hard drives?
Question 254
A security analyst is investigation an incident that was first reported as an issue connecting to network shares and the internet, While reviewing logs and tool output, the analyst sees the following:

Which of the following attacks has occurred?

Which of the following attacks has occurred?
Question 255
The IT department's on-site developer has been with the team for many years. Each time an application is released, the security team is able to identify multiple vulnerabilities. Which of the following would BEST help the team ensure the application is ready to be released to production?

