Question 266
While investigating a data leakage incident, a security analyst reviews access control to cloud-hosted dat a. The following information was presented in a security posture report.
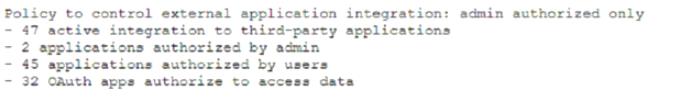
Based on the report, which of the following was the MOST likely attack vector used against the company?

Based on the report, which of the following was the MOST likely attack vector used against the company?
Question 267
A manufacturer creates designs for very high security products that are required to be protected and controlled by the government regulations. These designs are not accessible by corporate networks or the Internet. Which of the following is the BEST solution to protect these designs?
Question 268
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following:

Which of the following BEST describes the attack that was attempted against the forum readers?

Which of the following BEST describes the attack that was attempted against the forum readers?
Question 269
A network engineer notices the VPN concentrator overloaded and crashes on days when there are a lot of remote workers. Senior management has placed greater importance on the availability of VPN resources for the remote workers than the security of the end users' traffic. Which of the following would be BEST to solve this issue?
Question 270
A security analyst is reviewing the following attack log output:
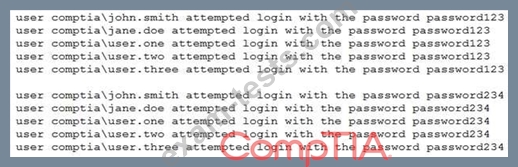
Which of the following types of attacks does this MOST likely represent?

Which of the following types of attacks does this MOST likely represent?

