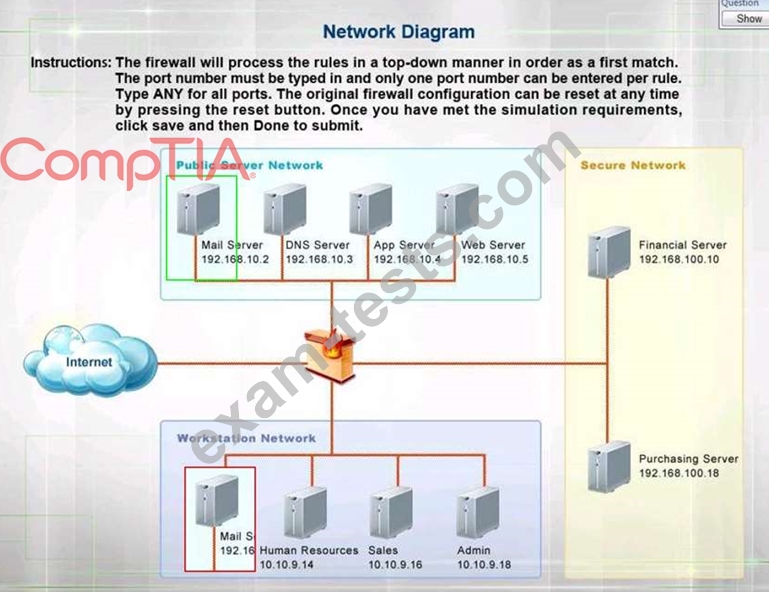
Question 141
While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below:
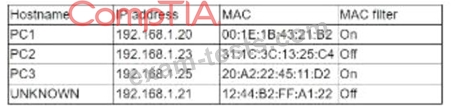
Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?

Which of the following should be the administrator's NEXT step to detect if there is a rogue system without impacting availability?
Question 142
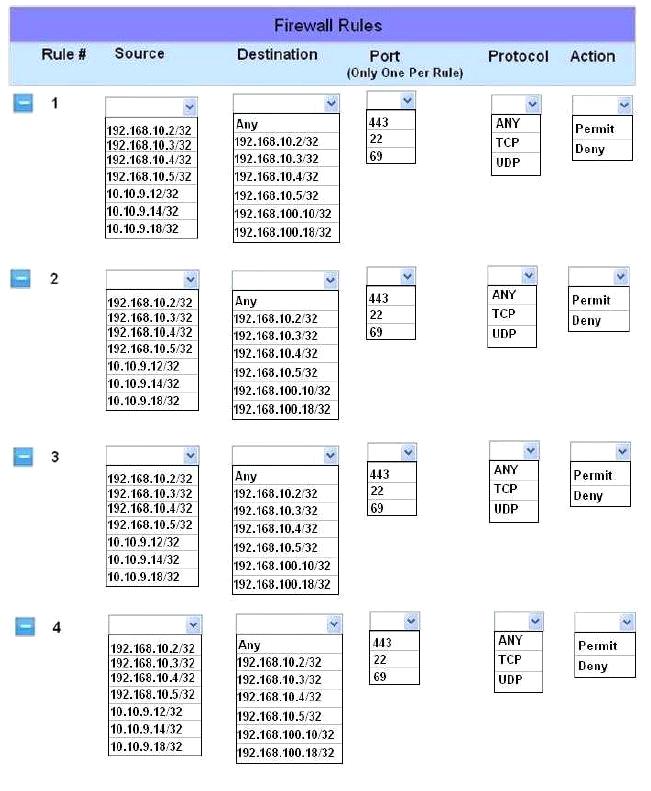
The security administrator has installed a new firewall which implements an implicit DENY policy by default.
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.
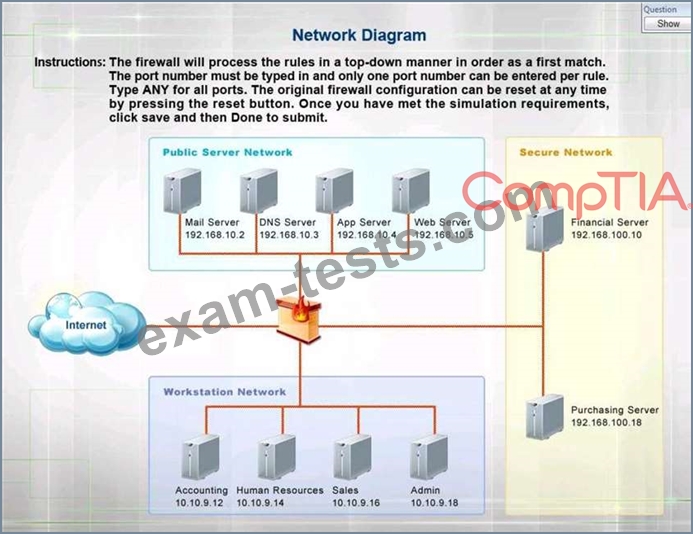
INSTRUCTIONS:
Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.

Question 143
A security administrator checks the table of a network switch, which shows the following output:
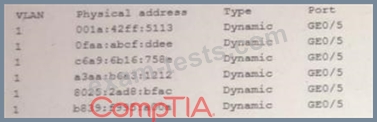
Which of the following is happening to this switch?

Which of the following is happening to this switch?
Question 144
A company needs to centralize its logs to create a baseline and have visibility on its security events. Which of the following technologies will accomplish this objective?
Question 145
A user enters a password to log in to a workstation and is then prompted to enter an authentication code.
Which of the following MFA factors or attributes are being utilized in the authentication process? (Select TWO).
Which of the following MFA factors or attributes are being utilized in the authentication process? (Select TWO).