Question 151
A security administrator needs to create a RAIS configuration that is focused on high read speeds and fault tolerance. It is unlikely that multiple drivers will fail simultaneously. Which of the following RAID configurations should the administration use?
Question 152
During an incident response, a security analyst observes the following log entry on the web server.
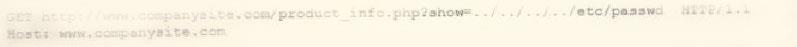
Which of the following BEST describes the type of attack the analyst is experience?
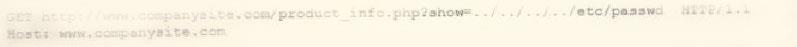
Which of the following BEST describes the type of attack the analyst is experience?
Question 153
A security analyst is investigating a vulnerability in which a default file permission was set incorrectly. The company uses non-credentialed scanning for vulnerability management.
Which of the following tools can the analyst use to verify the permissions?
Which of the following tools can the analyst use to verify the permissions?
Question 154
Which of the following are the MOST likely vectors for the unauthorized or unintentional inclusion of vulnerable code in a software company's final software releases? (Choose two.)
Question 155
Which of the following environments utilizes dummy data and is MOST likely to be installed locally on a system that allows code to be assessed directly and modified easily with each build?

