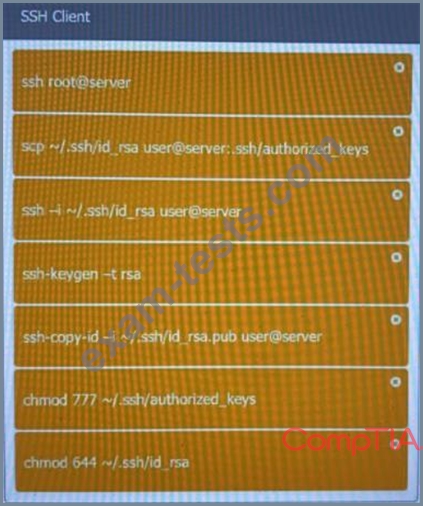
Question 161
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Question 162
An analyst visits an Internet forum looking for information about a tool. The analyst finds a thread that appears to contain relevant information. One of the posts says the following:
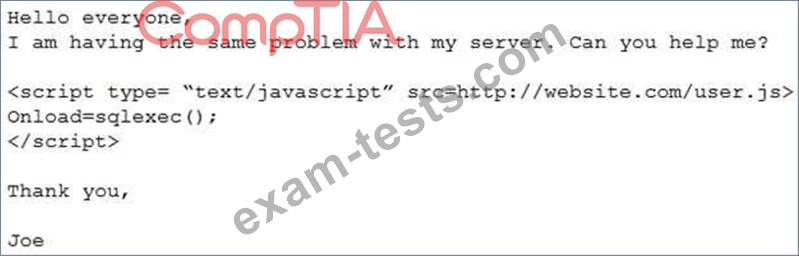
Which of the following BEST describes the attack that was attempted against the forum readers?

Which of the following BEST describes the attack that was attempted against the forum readers?
Question 163
A security analyst is reviewing the following attack log output:

Which of the following types of attacks does this MOST likely represent?

Which of the following types of attacks does this MOST likely represent?
Question 164
A network engineer at a company with a web server is building a new web environment with the following requirements:
Only one web server at a time can service requests.
If the primary web server fails, a failover needs to occur to ensure the secondary web server becomes the primary.
Which of the following load-balancing options BEST fits the requirements?
Only one web server at a time can service requests.
If the primary web server fails, a failover needs to occur to ensure the secondary web server becomes the primary.
Which of the following load-balancing options BEST fits the requirements?
Question 165
A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements:
* The devices will be used internationally by staff who travel extensively.
* Occasional personal use is acceptable due to the travel requirements.
* Users must be able to install and configure sanctioned programs and productivity suites.
* The devices must be encrypted
* The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?
* The devices will be used internationally by staff who travel extensively.
* Occasional personal use is acceptable due to the travel requirements.
* Users must be able to install and configure sanctioned programs and productivity suites.
* The devices must be encrypted
* The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?