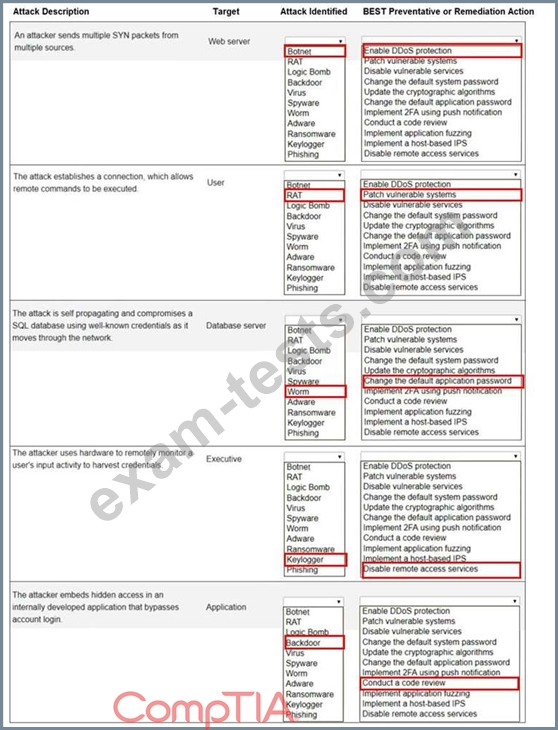
Question 156
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
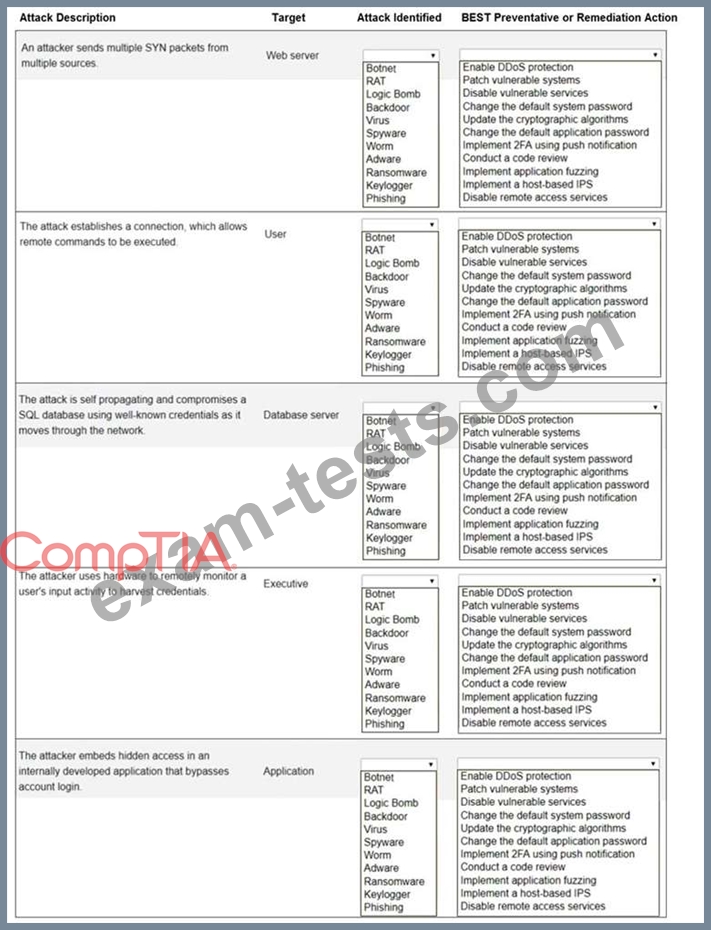
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Question 157
Which of the following must be in place before implementing a BCP?
Question 158
A workwide manufacturing company has been experiencing email account compromised. In one incident, a user logged in from the corporate office in France, but then seconds later, the same user account attempted a login from Brazil. Which of the following account policies would BEST prevent this type of attack?
Question 159
A security engineer at an offline government facility is concerned about the validity of an SSL certificate. The engineer wants to perform the fastest check with the least delay to determine if the certificate has been revoked. Which of the following would BEST these requirement?
Question 160
A large enterprise has moved all Hs data to the cloud behind strong authentication and encryption A sales director recently had a laptop stolen and later, enterprise data was round to have been compromised database.
Which of the following was the MOST likely cause?
Which of the following was the MOST likely cause?