Question 81
Refer to the following code:

Which of the following vulnerabilities would occur if this is executed?

Which of the following vulnerabilities would occur if this is executed?
Question 82
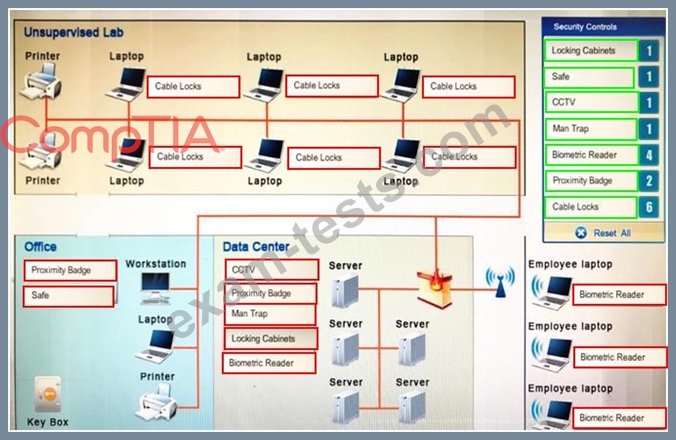
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.
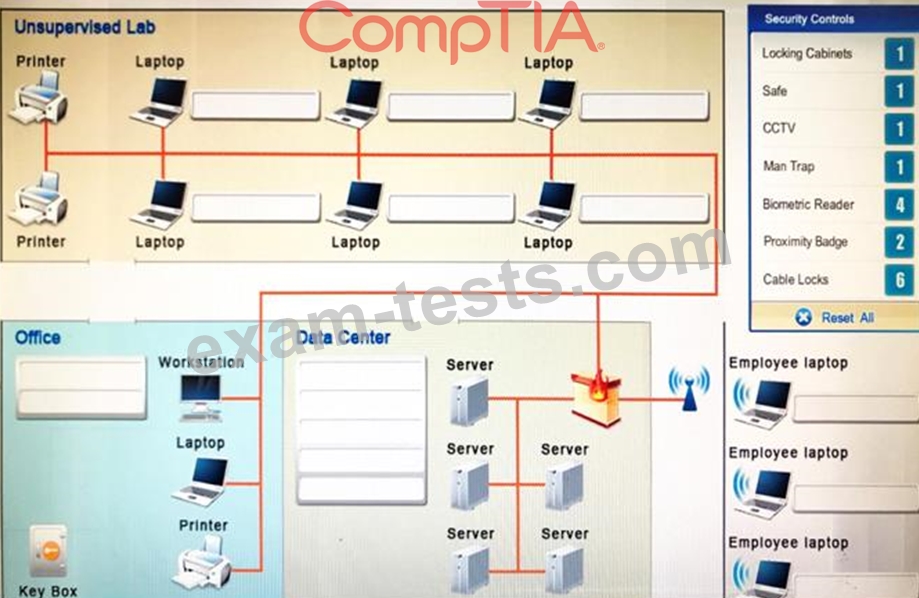
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.

Question 83
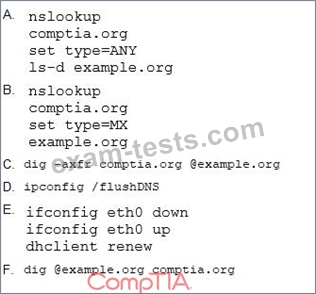
A security analyst is testing both Windows and Linux systems for unauthorized DNS zone transfers within a LAN on comptia.org from example.org. Which of the following commands should the security analyst use? (Select two.)

Question 84
A security team received reports of increased latency on a highly utilized e-commerce server. This led to eventual service unavailability as a result of internal scanning activity. The following web-server log was shared with the team to support this claim:
Which of the following actions would BEST address the service impact caused by scanning?
Which of the following actions would BEST address the service impact caused by scanning?
Question 85
A security administrator is working with the human resources department to classify data held by the company. The administrator has determined the data contains a variety of data types, including health information, employee names and addresses, trade secrets, and confidential customer information. Which of the following should the security administrator do NEXT?