Question 281
A company needs to implement an on-premises system that allows partner organizations to exchange order and inventory data electronically with the company over the Internet. The security architect must ensure the data is protected while minimizing the overhead associated with managing individual partner connections. Which of the following should the security architect recommend?
Question 282
A security administrator is configuring a RADIUS server for wireless authentication. The configuration must ensure client credentials are encrypted end-to-end between the client and the authenticator. Which of the following protocols should be configured on the RADIUS server?
(Select TWO.)
(Select TWO.)
Question 283
A network administrator needs to prevent users from accessing the accounting department records. All users are connected to the same Layer 2 device and access the Internet through the same router. Which of the following should be implemented to segment the accounting department from the rest of the users?
Question 284
Which of the following allows an application to securely authenticate a user by receiving credentials from a web domain?
Question 285
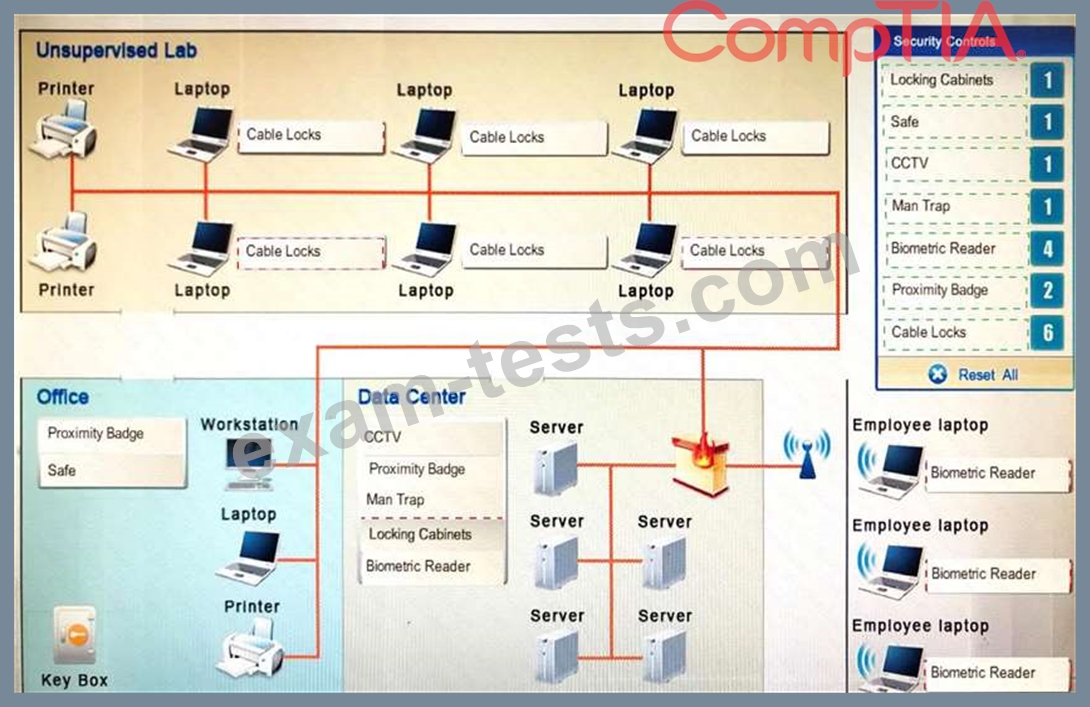
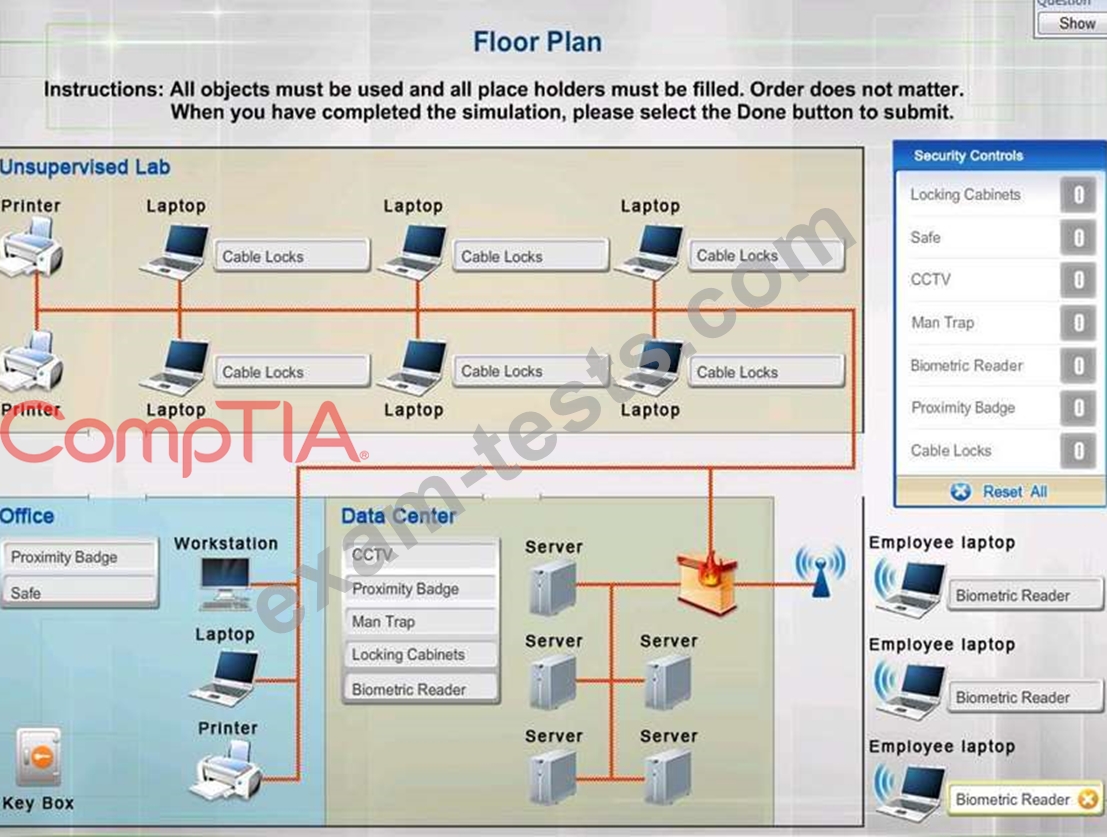
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.
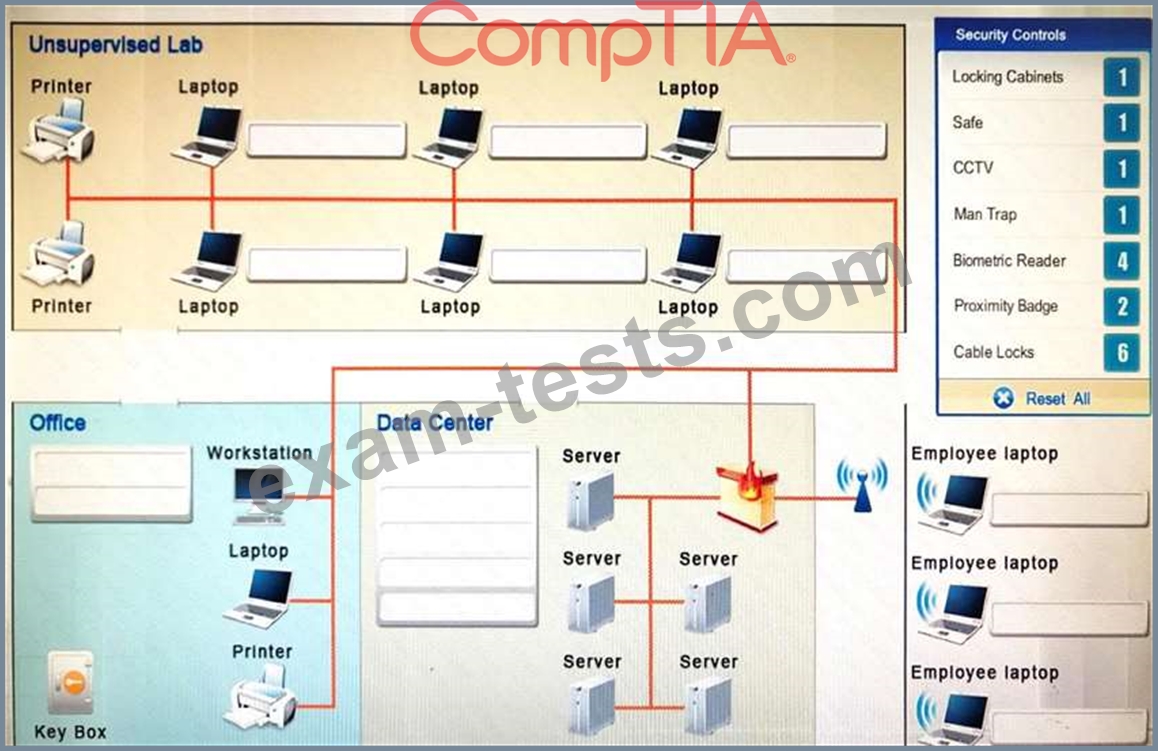
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.