Question 101
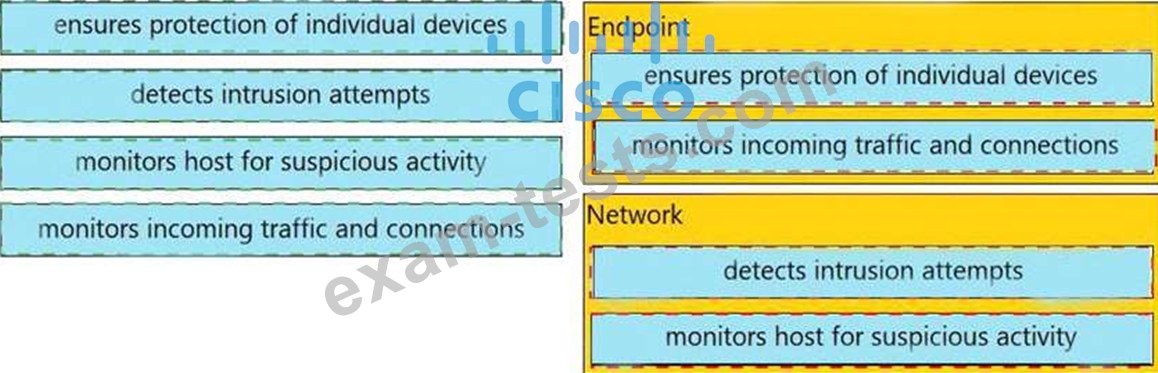
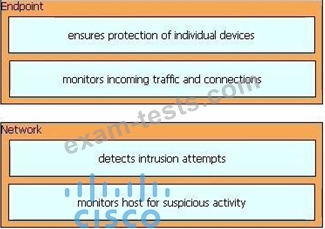
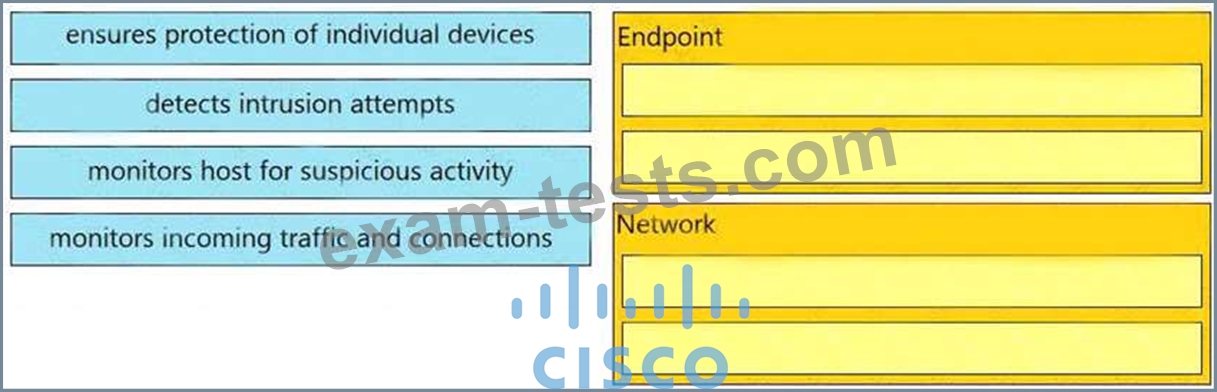
Drag and drop the uses on the left onto the type of security system on the right.

Question 102
A company encountered a breach on its web servers using IIS 7 5 Dunng the investigation, an engineer discovered that an attacker read and altered the data on a secure communication using TLS 1 2 and intercepted sensitive information by downgrading a connection to export-grade cryptography. The engineer must mitigate similar incidents in the future and ensure that clients and servers always negotiate with the most secure protocol versions and cryptographic parameters. Which action does the engineer recommend?
Question 103
Which technology prevents end-device to end-device IP traceability?
Question 104
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
What is the initial event called in the NIST SP800-61?
Question 105
What is an example of social engineering attacks?