Question 81
Refer to the exhibit.
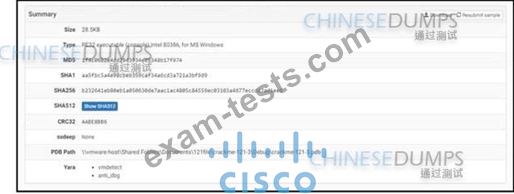
An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?

An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?
Question 82
What does cyber attribution identity in an investigation?
Question 83
An engineer is analyzing a recent breach where confidential documents were altered and stolen by the receptionist Further analysis shows that the threat actor connected an externa USB device to bypass security restrictions and steal data The engineer could not find an external USB device Which piece of information must an engineer use for attribution in an investigation?
Question 84
What is a difference between SIEM and SOAR?
Question 85
In a SOC environment, what is a vulnerability management metric?

