Question 86
Which system monitors local system operation and local network access for violations of a security policy?
Question 87
DRAG DROP
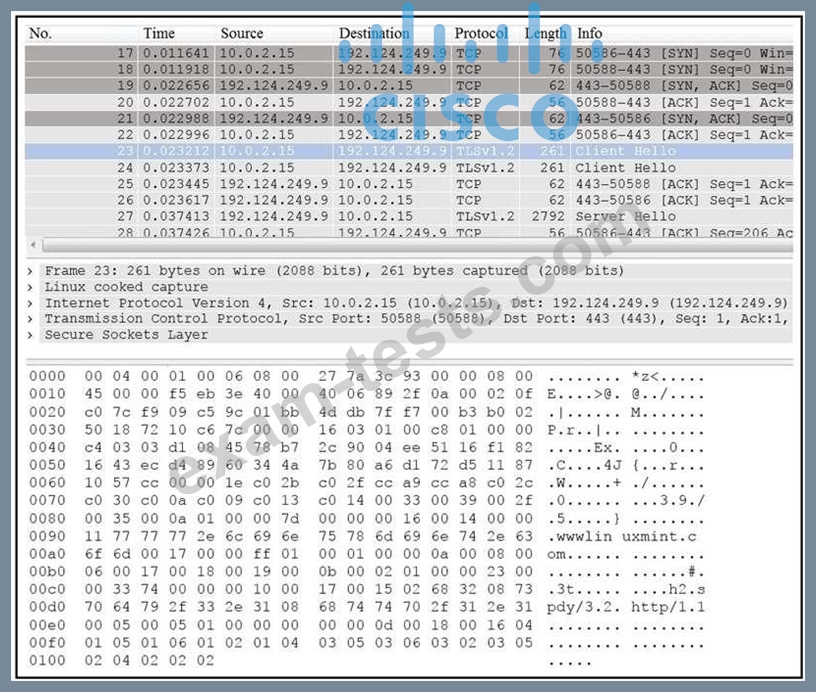
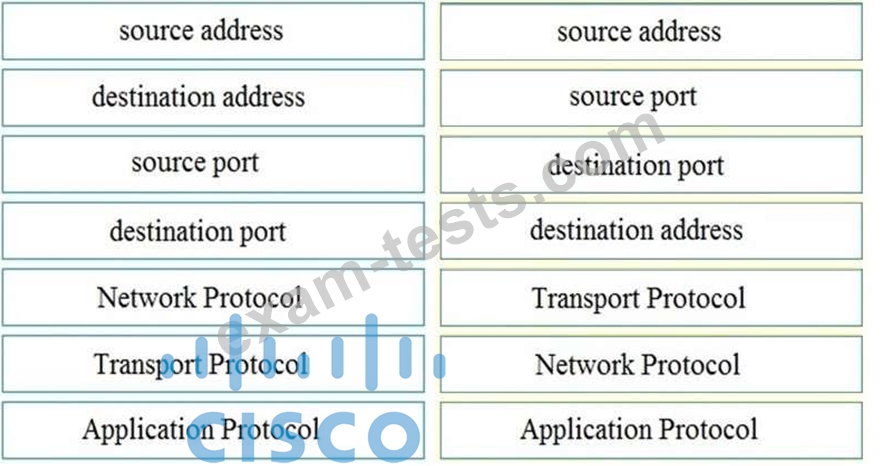
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
Select and Place:
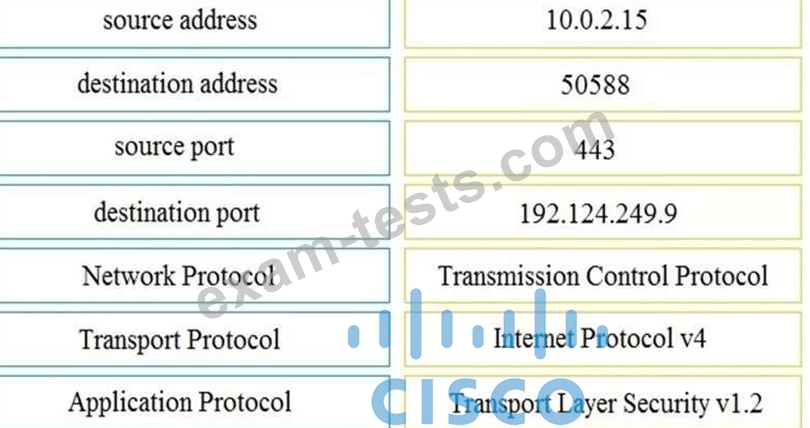

Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
Select and Place:

Question 88
Which incidence response step includes identifying all hosts affected by an attack'?
Question 89
What is the difference between a threat and a risk?
Question 90
Refer to the exhibit.
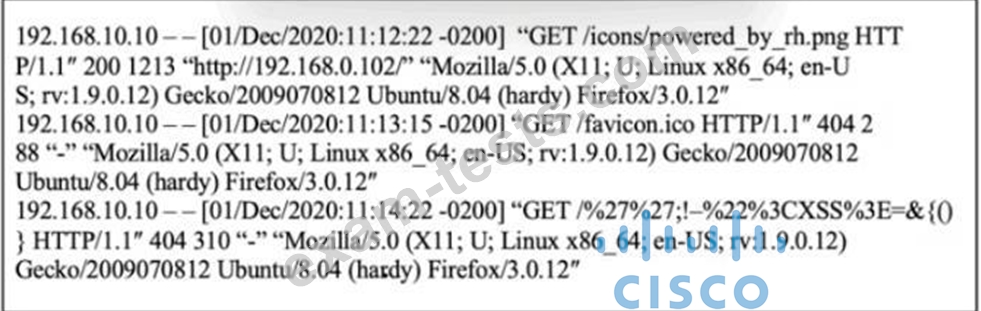
What is occurring?

What is occurring?