Question 106
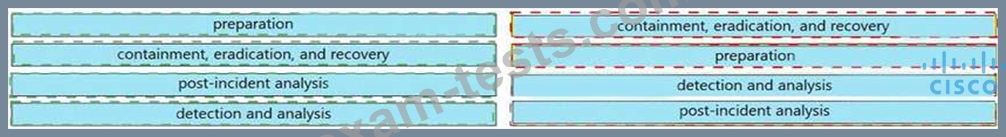
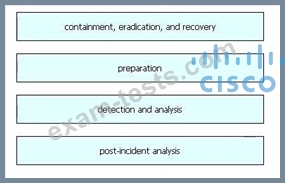
Drag and drop the elements from the left into the correct order for incident handling on the right.


Question 107
What does an attacker use to determine which network ports are listening on a potential target device?
Question 108
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
Which piece of information is needed to search for additional downloads of this file by other hosts?
Question 109
How does an SSL certificate impact security between the client and the server?
Question 110
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?