Question 121
What is rule-based detection when compared to statistical detection?
Question 122
Which two elements are used for profiling a network? (Choose two.)
Question 123
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication.
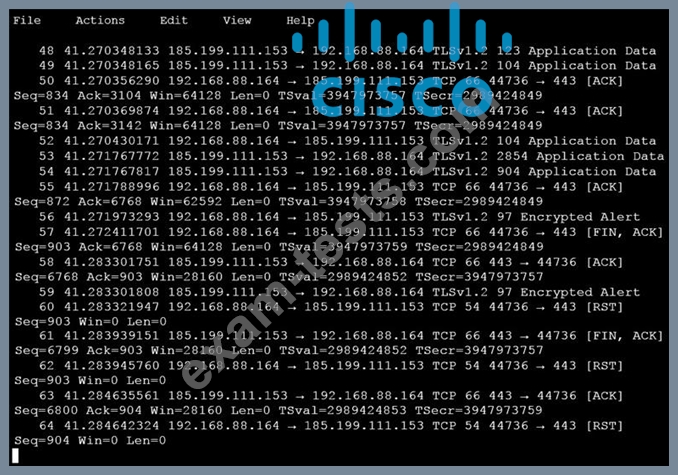
Which obfuscation technique is the attacker using?

Which obfuscation technique is the attacker using?
Question 124
An organization's security team has detected network spikes coming from the internal network. An investigation has concluded that the spike in traffic was from intensive network scanning How should the analyst collect the traffic to isolate the suspicious host?
Question 125
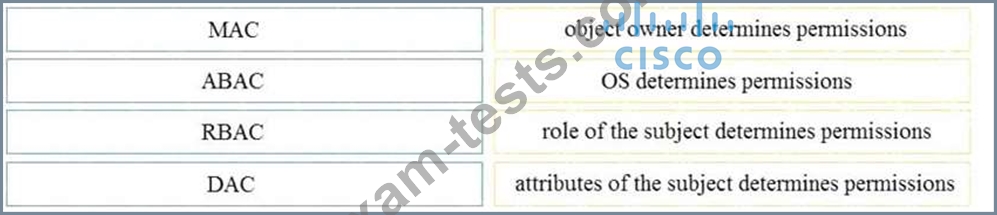
Drag and drop the access control models from the left onto the correct descriptions on the right.