Question 11
Why is encryption challenging to security monitoring?
Question 12
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
* If the process is unsuccessful, a negative value is returned.
* If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?
* If the process is unsuccessful, a negative value is returned.
* If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?
Question 13
Refer to the exhibit.

A network administrator is investigating suspicious network activity by analyzing captured traffic. An engineer notices abnormal behavior and discovers that the default user agent is present in the headers of requests and data being transmitted What is occurring?

A network administrator is investigating suspicious network activity by analyzing captured traffic. An engineer notices abnormal behavior and discovers that the default user agent is present in the headers of requests and data being transmitted What is occurring?
Question 14
Which attack method intercepts traffic on a switched network?
Question 15
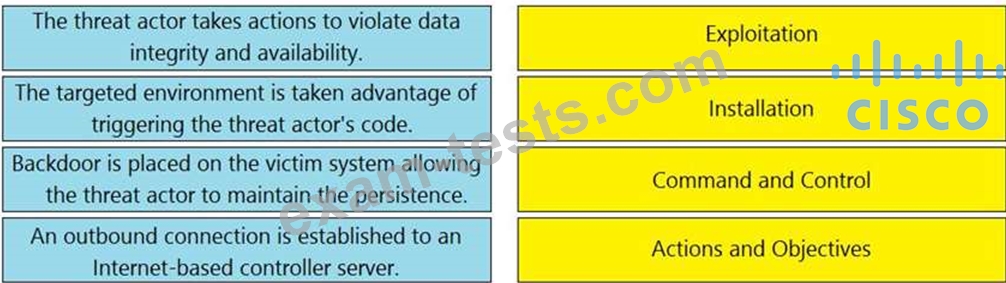
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.