Question 36
An analyst is investigating an incident in a SOC environment.
Which method is used to identify a session from a group of logs?
Which method is used to identify a session from a group of logs?
Question 37
Refer to the exhibit.
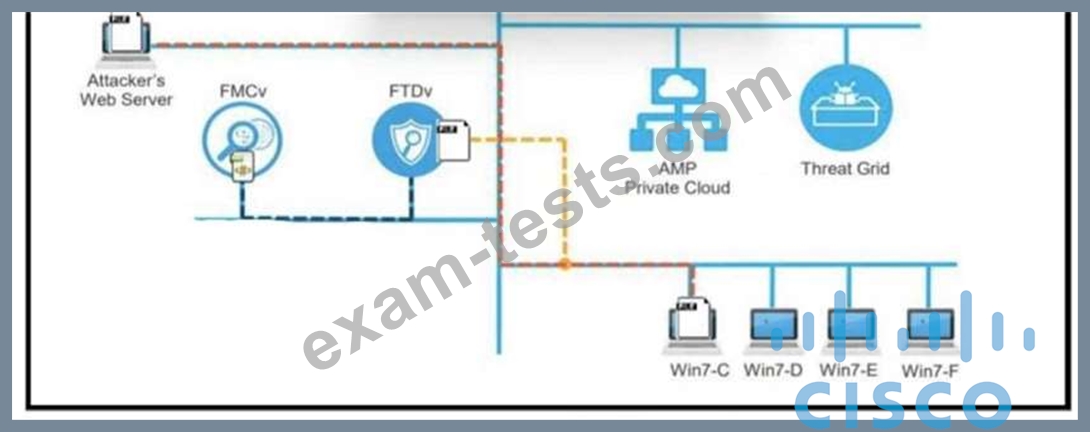
A workstation downloads a malicious docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the tile event is recorded What would have occurred with stronger data visibility?

A workstation downloads a malicious docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the tile event is recorded What would have occurred with stronger data visibility?
Question 38
Refer to the exhibit.
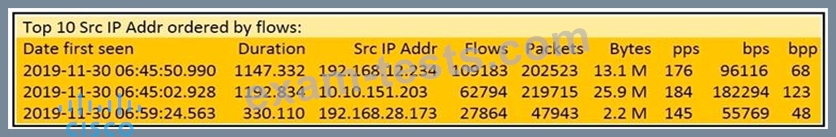
What information is depicted?

What information is depicted?
Question 39
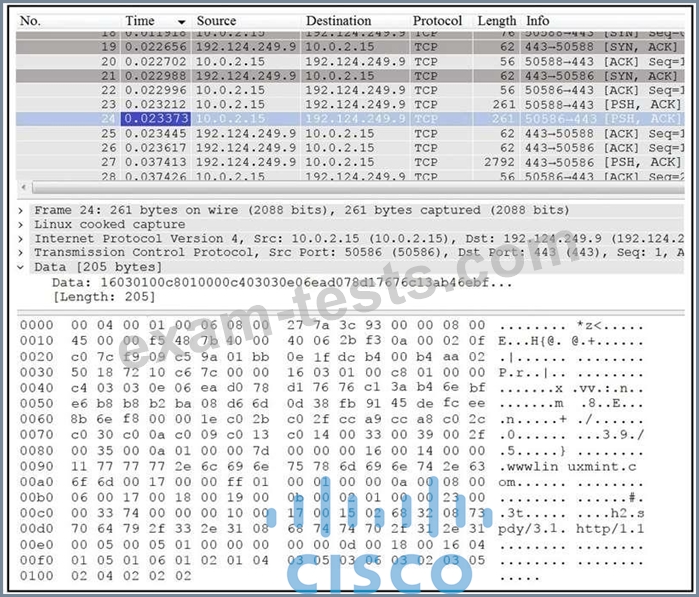
Refer to the exhibit. Which application protocol is in this PCAP file?
Question 40
One of the objectives of information security is to protect the CIA of information and systems.
What does CIA mean in this context?
What does CIA mean in this context?

