Question 31
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email.
When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
Question 32
What is an attack surface as compared to a vulnerability?
Question 33
Refer to the exhibit.
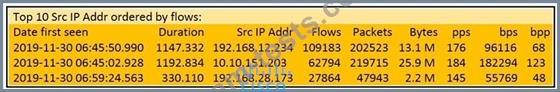
What information is depicted?

What information is depicted?
Question 34
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
Question 35
Refer to the exhibit.

Which type of log is displayed?

Which type of log is displayed?

