Question 21
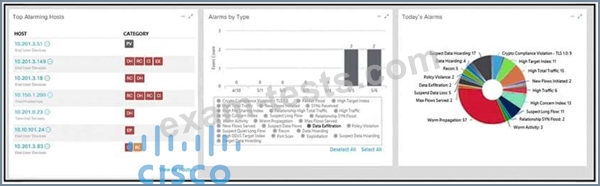
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
Question 22
Which type of access control depends on the job function of the user?
Question 23
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
Question 24
How does an attack surface differ from an attack vector?
Question 25
Which action prevents buffer overflow attacks?

