Question 41
What is a benefit of using asymmetric cryptography?
Question 42
Refer to the exhibit.

Which type of log is displayed?

Which type of log is displayed?
Question 43
Which security monitoring data type requires the largest storage space?
Question 44
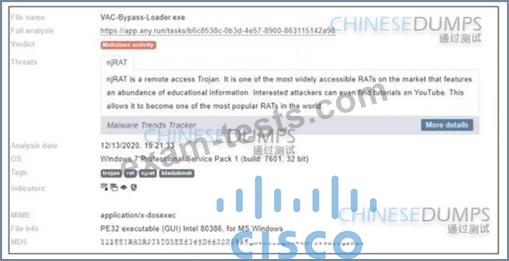
Refer to the exhibit. Where is the executable file?
Question 45
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
Which technology should be used to accomplish this task?

