Question 66
A company is in the process of outsourcing its customer relationship management system to a cloud provider. It will host the entire organization's customer database. The database will be accessed by both the company's users and its customers. The procurement department has asked what security activities must be performed for the deal to proceed. Which of the following are the MOST appropriate security activities to be performed as part of due diligence? (Select TWO).
Question 67
An organization has just released a new mobile application for its customers.
The application has an inbuilt browser and native application to render content from existing websites and the organization's new web services gateway.
All rendering of the content is performed on the mobile application.
The application requires SSO between the application, the web services gateway and legacy UI.
Which of the following controls MUST be implemented to securely enable SSO?
The application has an inbuilt browser and native application to render content from existing websites and the organization's new web services gateway.
All rendering of the content is performed on the mobile application.
The application requires SSO between the application, the web services gateway and legacy UI.
Which of the following controls MUST be implemented to securely enable SSO?
Question 68
A recent CRM upgrade at a branch office was completed after the desired deadline.
Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded. Which of the following should be used to identify weak processes and other vulnerabilities?
Several technical issues were found during the upgrade and need to be discussed in depth before the next branch office is upgraded. Which of the following should be used to identify weak processes and other vulnerabilities?
Question 69
A new database application was added to a company's hosted VM environment. Firewall ACLs were modified to allow database users to access the server remotely. The company's cloud security broker then identified abnormal from a database user on-site. Upon further investigation, the security team noticed the user ran code on a VM that provided access to the hypervisor directly and access to other sensitive data.
Which of the following should the security do to help mitigate future attacks within the VM environment? (Choose two.)
Which of the following should the security do to help mitigate future attacks within the VM environment? (Choose two.)
Question 70
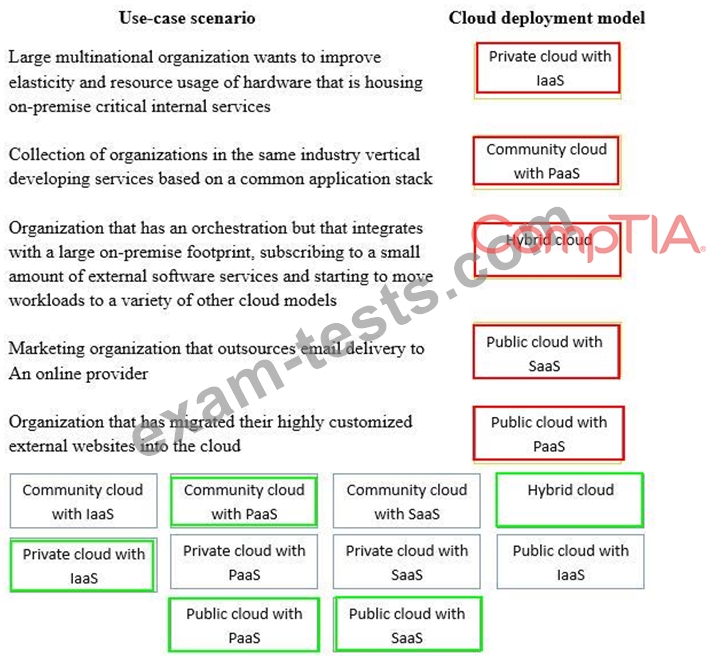
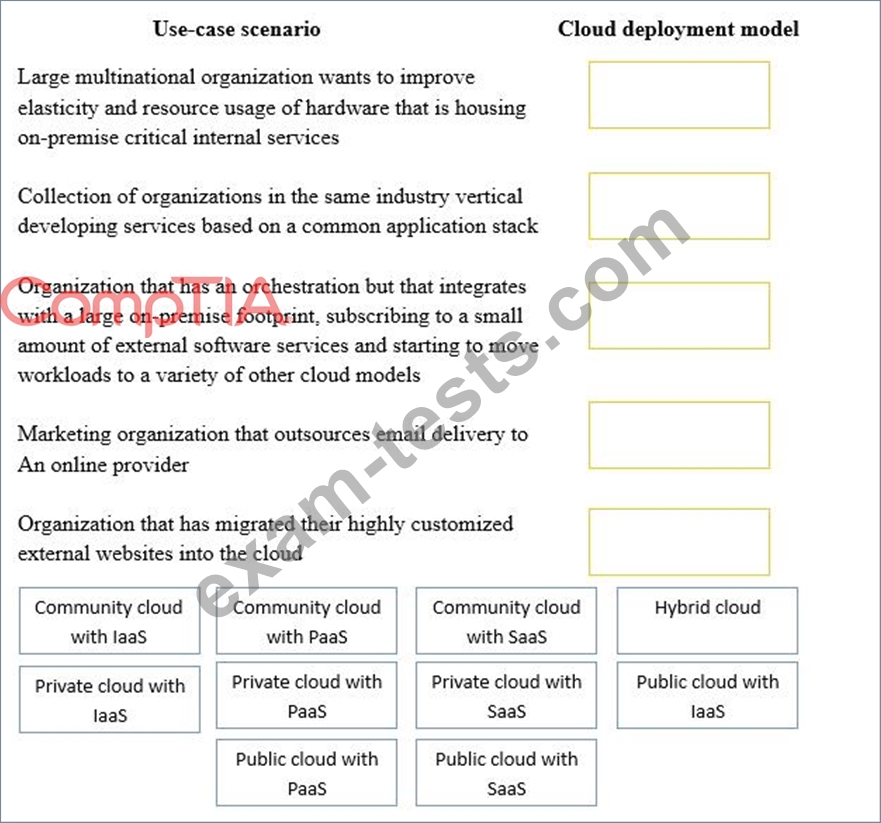
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.

Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here: