Question 76
A security consultant is improving the physical security of a sensitive site and takes pictures of the unbranded building to include in the report. Two weeks later, the security consultant misplaces the phone, which only has one hour of charge left on it. The person who finds the phone removes the MicroSD card in an attempt to discover the owner to return it.
The person extracts the following data from the phone and EXIF data from some files:
DCIM Images folder
Audio books folder
Torrentz
My TAX.xls
Consultancy HR Manual.doc
Camera: SM-G950F
Exposure time: 1/60s
Location: 3500 Lacey Road USA
Which of the following BEST describes the security problem?
The person extracts the following data from the phone and EXIF data from some files:
DCIM Images folder
Audio books folder
Torrentz
My TAX.xls
Consultancy HR Manual.doc
Camera: SM-G950F
Exposure time: 1/60s
Location: 3500 Lacey Road USA
Which of the following BEST describes the security problem?
Question 77
A project manager is working with system owners to develop maintenance windows for system patching and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
Question 78
A hospital uses a legacy electronic medical record system that requires multicast for traffic between the application servers and databases on virtual hosts that support segments of the application. Following a switch upgrade, the electronic medical record is unavailable despite physical connectivity between the hypervisor and the storage being in place. The network team must enable multicast traffic to restore access to the electronic medical record. The ISM states that the network team must reduce the footprint of multicast traffic on the network.
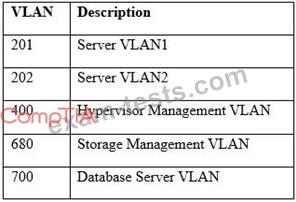
Using the above information, on which VLANs should multicast be enabled?

Using the above information, on which VLANs should multicast be enabled?
Question 79
A company has adopted and established a continuous-monitoring capability, which has proven to be
effective in vulnerability management, diagnostics, and mitigation. The company wants to increase the
likelihood that it is able to discover and therefore respond to emerging threats earlier in the life cycle.
Which of the following methodologies would BEST help the company to meet this objective? (Choose two.)
effective in vulnerability management, diagnostics, and mitigation. The company wants to increase the
likelihood that it is able to discover and therefore respond to emerging threats earlier in the life cycle.
Which of the following methodologies would BEST help the company to meet this objective? (Choose two.)
Question 80
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancements to the company's cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices.
Which of the following industry references is appropriate to accomplish this?
Which of the following industry references is appropriate to accomplish this?

