Question 71
A government organization operates and maintains several ICS environments. The categorization of one of the ICS environments led to a moderate baseline. The organization has complied a set of applicable security controls based on this categorization.
Given that this is a unique environment, which of the following should the organization do NEXT to determine if other security controls should be considered?
Given that this is a unique environment, which of the following should the organization do NEXT to determine if other security controls should be considered?
Question 72
A vulnerability was recently announced that allows a malicious user to gain root privileges on other virtual machines running within the same hardware cluster. Customers of which of the following cloud-based solutions should be MOST concerned about this vulnerability?
Question 73
A company provides on-demand cloud computing resources for a sensitive project. The company implements a fully virtualized datacenter and terminal server access with two- factor authentication for customer access to the administrative website. The security administrator at the company has uncovered a breach in data confidentiality. Sensitive data from customer A was found on a hidden directory within the VM of company B.
Company B is not in the same industry as company A and the two are not competitors. Which of the following has MOST likely occurred?
Company B is not in the same industry as company A and the two are not competitors. Which of the following has MOST likely occurred?
Question 74
It has come to the IT administrator's attention that the "post your comment" field on the company blog page has been exploited, resulting in cross-site scripting attacks against customers reading the blog. Which of the following would be the MOST effective at preventing the "post your comment" field from being exploited?
Question 75
A user workstation was infected with a new malware variant as a result of a drive-by download. The security administrator reviews key controls on the infected workstation and discovers the following:
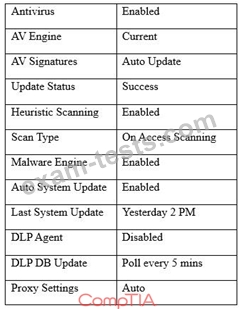
Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)

Which of the following would BEST prevent the problem from reoccurring in the future? (Choose two.)
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

