Question 56
The Chief Information Security Officer (CISO) of an established security department, identifies a customer who has been using a fraudulent credit card. The CISO calls the local authorities, and when they arrive on-site, the authorities ask a security engineer to create a point-in-time copy of the running database in their presence. This is an example of:
Question 57
A PaaS provider deployed a new product using a DevOps methodology Because DevOps is used to support both development and production assets inherent separation of duties is limited To ensure compliance with security frameworks that require a specific set of controls relating to separation of duties the organization must design and implement an appropriate compensating control Which of the following would be MOST suitable in this scenario?
Question 58
An insurance company has two million customers and is researching the top transactions on its customer portal. It identifies that the top transaction is currently password reset. Due to users not remembering their secret questions, a large number of calls are consequently routed to the contact center for manual password resets. The business wants to develop a mobile application to improve customer engagement in the future, continue with a single factor of authentication, minimize management overhead of the solution, remove passwords, and eliminate to the contact center.
Which of the following techniques would BEST meet the requirements? (Choose two.)
Which of the following techniques would BEST meet the requirements? (Choose two.)
Question 59
A project manager is working with a software development group to collect and evaluate user stories related to the organization's internally designed CRM tool. After defining requirements, the project manager would like to validate the developer's interpretation and understanding of the user's request. Which of the following would BEST support this objective?
Question 60
Joe an application security engineer is performing an audit of an environmental control application He has implemented a robust SDLC process and is reviewing API calls available to the application During the review. Joe finds the following in a log file.
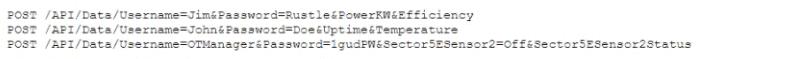
Which of the following would BEST mitigate the issue Joe has found?

Which of the following would BEST mitigate the issue Joe has found?

