Question 31
Company leadership believes employees are experiencing an increased number of cyber attacks; however, the metrics do not show this. Currently, the company uses "Number of successful phishing attacks" as a KRI, but it does not show an increase.
Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
Question 32
A remote user reports the inability to authenticate to the VPN concentrator. During troubleshooting, a security administrate captures an attempted authentication and discovers the following being presented by the user's VPN client:
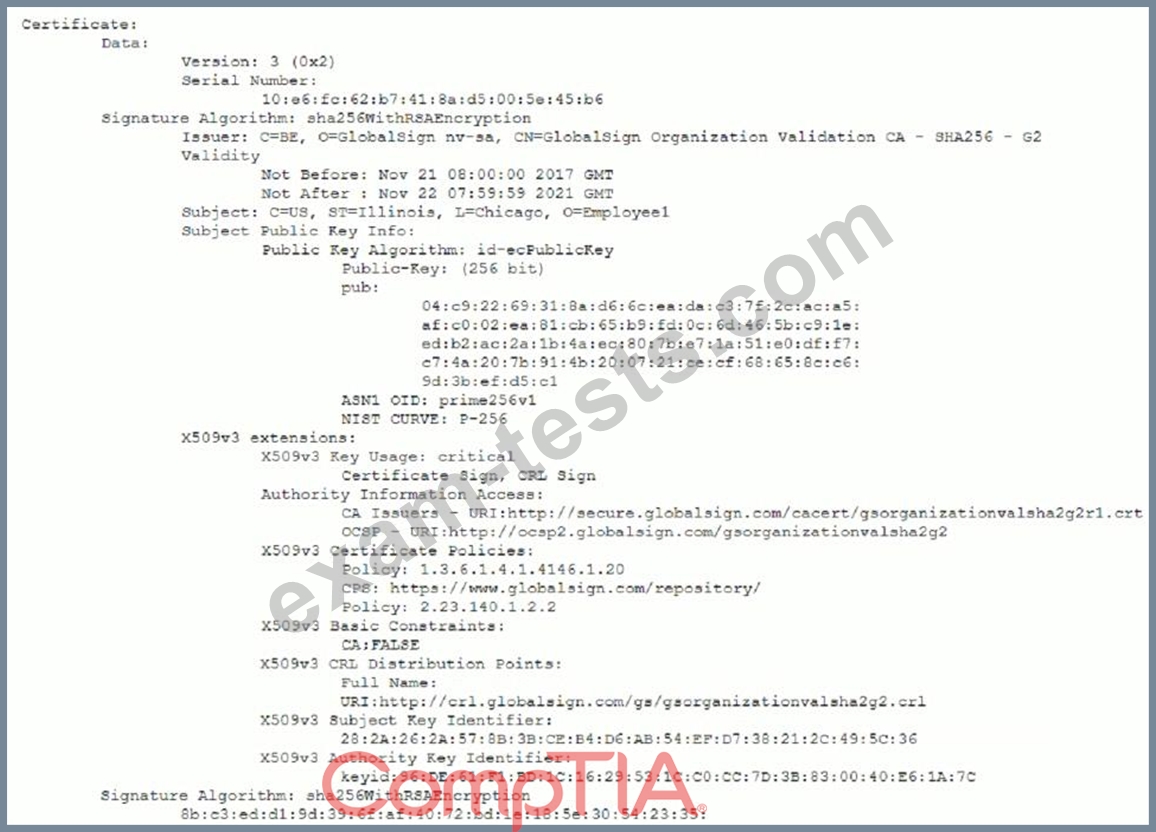
Which of the following BEST describes the reason the user is unable to connect to the VPN service?

Which of the following BEST describes the reason the user is unable to connect to the VPN service?
Question 33
A project manager is working with system owners to develop maintenance windows for system pathing and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
Question 34
During a recent incident, sensitive data was disclosed and subsequently destroyed through a properly secured, cloud-based storage platform. An incident response technician is working with management to develop an after action report that conveys critical metrics regarding the incident.
Which of the following would be MOST important to senior leadership to determine the impact of the breach?
Which of the following would be MOST important to senior leadership to determine the impact of the breach?
Question 35
A security engineer is making certain URLs from an internal application available on the Internet The development team requires the following
* The URLs are accessible only from internal IP addresses
* Certain countries are restricted
* TLS is implemented.
* System users transparently access internal application services in a round robin to maximize performance Which of the following should the security engineer deploy7
* The URLs are accessible only from internal IP addresses
* Certain countries are restricted
* TLS is implemented.
* System users transparently access internal application services in a round robin to maximize performance Which of the following should the security engineer deploy7

