Question 61
A company wants to extend its help desk availability beyond business hours. The Chief Information Officer (CIO) decides to augment the help desk with a third-party service that will answer calls and provide Tier 1 problem resolution, such as password resets and remote assistance. The security administrator implements the following firewall change:
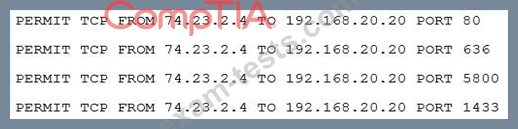
The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?

The administrator provides the appropriate path and credentials to the third-party company. Which of the following technologies is MOST likely being used to provide access to the third company?
Question 62
A security administrator is hardening a TrustedSolaris server that processes sensitive dat a. The data owner has established the following security requirements:
The data is for internal consumption only and shall not be distributed to outside individuals The systems administrator should not have access to the data processed by the server The integrity of the kernel image is maintained Which of the following host-based security controls BEST enforce the data owner's requirements? (Choose three.)
The data is for internal consumption only and shall not be distributed to outside individuals The systems administrator should not have access to the data processed by the server The integrity of the kernel image is maintained Which of the following host-based security controls BEST enforce the data owner's requirements? (Choose three.)
Question 63
A security appliance vendor is reviewing an RFP that is requesting solutions for the defense of a set of web-based applications. This RFP is from a financial institution with very strict performance requirements. The vendor would like to respond with its solutions.
Before responding, which of the following factors is MOST likely to have an adverse effect on the vendor's qualifications?
Before responding, which of the following factors is MOST likely to have an adverse effect on the vendor's qualifications?
Question 64
A systems administrator receives an advisory email that a recently discovered exploit is being used in another country and the financial institutions have ceased operations while they find a way to respond to the attack. Which of the following BEST describes where the administrator should look to find information on the attack to determine if a response must be prepared for the systems? (Choose two.)
Question 65
A company contracts a security consultant to perform a remote white-box penetration test. The company wants the consultant to focus on Internet-facing services without negatively impacting production services Which of the following is the consultant MOST likely to use to identify the company's attack surface? (Select TWO)
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

