Question 51
A security is testing a server finds the following in the output of a vulnerability scan:
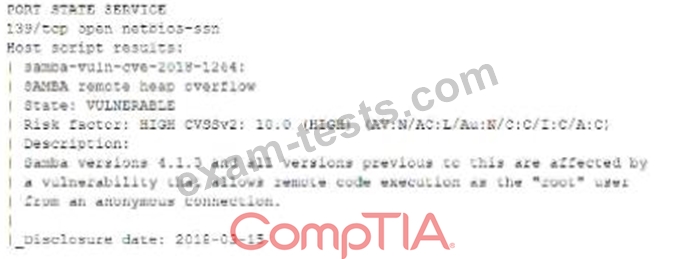
Which of the following will the security analyst most likely use NEXT to explore this further?

Which of the following will the security analyst most likely use NEXT to explore this further?
Question 52
A healthcare company wants to increase the value of the data it collects on its patients by making the data available to third-party researchers for a fee Which of the following BEST mitigates the risk to the company?
Question 53
Which of the following is the GREATEST security concern with respect to BYOD?
Question 54
An organization is moving internal core data-processing functions related to customer data to a global public cloud provider that uses aggregated services from other partner organizations. Which of the following compliance issues will MOST likely be introduced as a result of the migration?
Question 55
A technician is configuring security options on the mobile device manager for users who often utilize public Internet connections while travelling. After ensuring that full disk encryption is enabled, which of the following security measures should the technician take? (Choose two.)
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

