Question 41
A newly hired systems administrator is trying to connect a new and fully updated, but very customized, Android device to access corporate resources. However, the MDM enrollment process continually fails. The administrator asks a security team member to look into the issue.
Which of the following is the MOST likely reason the MDM is not allowing enrollment?
Which of the following is the MOST likely reason the MDM is not allowing enrollment?
Question 42
A systems administrator has installed a disk wiping utility on all computers across the organization and configured it to perform a seven-pass wipe and an additional pass to overwrite the disk with zeros. The company has also instituted a policy that requires users to erase files containing sensitive information when they are no longer needed.
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:

Which of the following should be included in the auditor's report based on the above findings?
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:

Which of the following should be included in the auditor's report based on the above findings?
Question 43
While investigating suspicious activity on a server, a security administrator runs the following report:
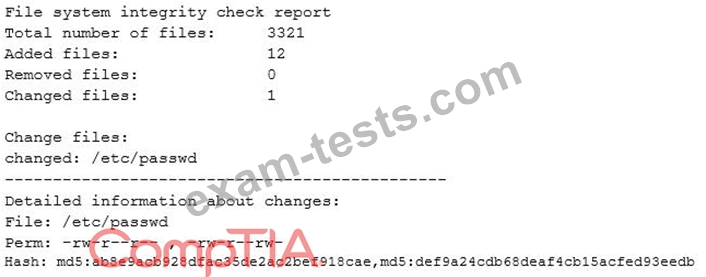
In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describe this scenario? (Choose two.)

In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describe this scenario? (Choose two.)
Question 44
A company has made it a spending priority to implement security architectures that will be resilient during an attack. Recent incidents have involved attackers leveraging latent vulnerabilities in cryptographic implementations and VPN concentrators to be able to compromise sensitive information. Patches have been slowly released for these emergent vulnerabilities, leaving weeks to months of exposed and vulnerable attack surface. Which of the following approaches would be BEST to increase enterprise resilience during similar future attacks?
Question 45
A new cluster of virtual servers has been set up in a lab environment and must be audited before being allowed on the production network. The security manager needs to ensure unnecessary services are disabled and all system accounts are using strong credentials.
Which of the following tools should be used? (Choose two.)
Which of the following tools should be used? (Choose two.)

