Question 11
A company is concerned about disgruntled employees transferring its intellectual property data through covert channels. Which of the following tools would allow employees to write data into ICMP echo response packets?
Question 12
A cybersecurity analyst is conducting packet analysis on the following:
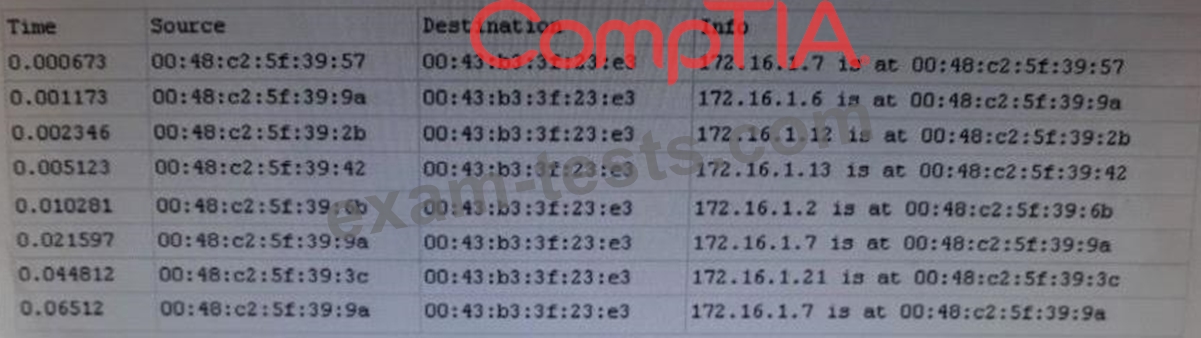
Which of the following is occurring in the given packet capture?

Which of the following is occurring in the given packet capture?
Question 13
A security consultant was hired to audit a company's password are account policy. The company implements the following controls:
Minimum password length: 16
Maximum password age: 0
Minimum password age: 0
Password complexity: disabled
Store passwords in plain text: disabled
Failed attempts lockout: 3
Lockout timeout: 1 hour
The password database uses salted hashes and PBKDF2. Which of the following is MOST likely to yield the greatest number of plain text passwords in the shortest amount of time?
Minimum password length: 16
Maximum password age: 0
Minimum password age: 0
Password complexity: disabled
Store passwords in plain text: disabled
Failed attempts lockout: 3
Lockout timeout: 1 hour
The password database uses salted hashes and PBKDF2. Which of the following is MOST likely to yield the greatest number of plain text passwords in the shortest amount of time?
Question 14
A security engineer is helping the web developers assess a new corporate web application The application will be Internet facing so the engineer makes the following recommendation:
In an htaccess file or the site config add:
or add to the location block:
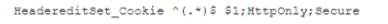
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
In an htaccess file or the site config add:
or add to the location block:
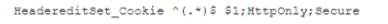
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
Question 15
An engineer is assisting with the design of a new virtualized environment that will house critical company services and reduce the datacenter's physical footprint. The company has expressed concern about the integrity of operating systems and wants to ensure a vulnerability exploited in one datacenter segment would not lead to the compromise of all others.
Which of the following design objectives should the engineer complete to BEST mitigate the company's concerns? (Choose two.)
Which of the following design objectives should the engineer complete to BEST mitigate the company's concerns? (Choose two.)

