Question 26
Click on the exhibit buttons to view the four messages.

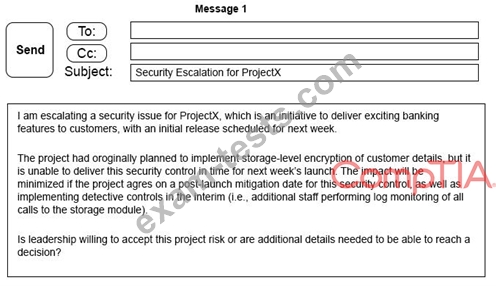
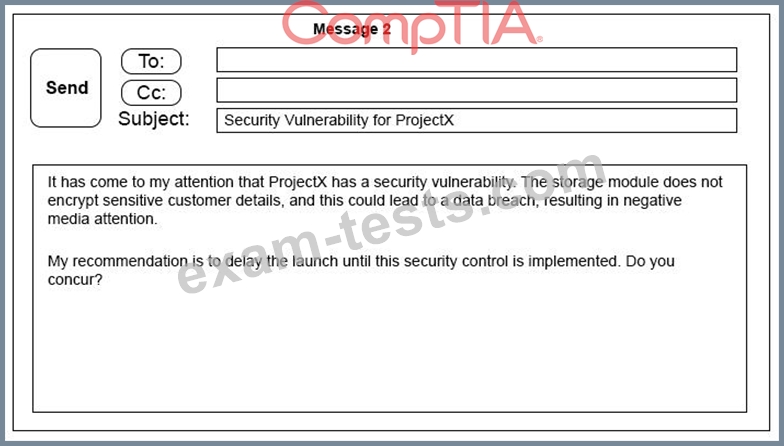
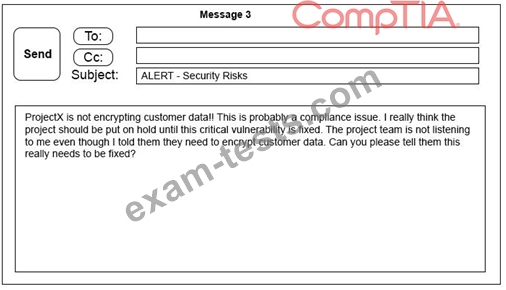

A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership.
Which of the following BEST conveys the business impact for senior leadership?





A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records. The security architect is drafting an escalation email to senior leadership.
Which of the following BEST conveys the business impact for senior leadership?
Question 27
A large organization suffers a data breach after one staff member inadvertently shares a document on a corporate-approved, file-sharing, cloud-collaboration service. The security administrator must implement controls to reduce the likelihood of a similar event, via another channel, from occurring again. The controls also must assist with early detection and remediation should the event reoccur.
The organization has the following enterprise constraints:
1. On-premises proxies are used to control access to websites.
2 Some staff work remotely from home and connect directly to the Internet without a VPN.
3. Corporate firewalls send logs to a central log aggregator.
4. More than 40,000 staff members are distributed across two core buildings and 100 small branches.
Which of the following would BEST meet the requirements? (Select THREE).
The organization has the following enterprise constraints:
1. On-premises proxies are used to control access to websites.
2 Some staff work remotely from home and connect directly to the Internet without a VPN.
3. Corporate firewalls send logs to a central log aggregator.
4. More than 40,000 staff members are distributed across two core buildings and 100 small branches.
Which of the following would BEST meet the requirements? (Select THREE).
Question 28
An organization wants to allow its employees to receive corporate email on their own smartphones. A security analyst is reviewing the following information contained within the file system of an employee's smartphone:
FamilyPix.jpg
Taxreturn.tax
paystub.pdf
employeesinfo.xls
SoccerSchedule.doc
RecruitmentPlan.xls
Based on the above findings, which of the following should the organization implement to prevent further exposure? (Select two).
FamilyPix.jpg
Taxreturn.tax
paystub.pdf
employeesinfo.xls
SoccerSchedule.doc
RecruitmentPlan.xls
Based on the above findings, which of the following should the organization implement to prevent further exposure? (Select two).
Question 29
A security engineer is assessing a new IoT product. The product interfaces with the ODBII port of a vehicle and uses a Bluetooth connection to relay data to an onboard data logger located in the vehicle. The data logger can only transfer data over a custom USB cable. The engineer suspects a relay attack is possible against the cryptographic implementation used to secure messages between segments of the system. Which of the following tools should the engineer use to confirm the analysis?
Question 30
During the deployment of a new system, the implementation team determines that APIs used to integrate the new system with a legacy system are not functioning properly. Further investigation shows there is a misconfigured encryption algorithm used to secure data transfers between systems. Which of the following should the project manager use to determine the source of the defined algorithm in use?

