Question 21
A security administrator is updating corporate policies to respond to an incident involving collusion between two systems administrators that went undetected for more than six months.
Which of the following policies would have MOST likely uncovered the collusion sooner? (Choose two.)
Which of the following policies would have MOST likely uncovered the collusion sooner? (Choose two.)
Question 22
A large company with a very complex IT environment is considering a move from an on-premises, internally managed proxy to a cloud-based proxy solution managed by an external vendor. The current proxy provides caching, content filtering, malware analysis, and URL categorization for all staff connected behind the proxy. Staff members connect directly to the Internet outside of the corporate network. The cloud-based version of the solution would provide content filtering, TLS decryption, malware analysis, and URL categorization. After migrating to the cloud solution, all internal proxies would be decommissioned. Which of the following would MOST likely change the company's risk profile?
Question 23
The code snippet below controls all electronic door locks to a secure facility in which the doors should only fail open in an emergency. In the code, "criticalValue" indicates if an emergency is underway:
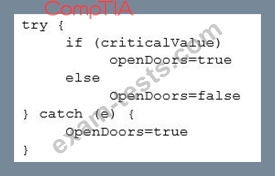
Which of the following is the BEST course of action for a security analyst to recommend to the software developer?

Which of the following is the BEST course of action for a security analyst to recommend to the software developer?
Question 24
A developer is reviewing the following transaction logs from a web application:
Username: John Doe
Street name: Main St.
Street number: <script>alert('test')</alert>
Which of the following code snippets should the developer implement given the above transaction logs?
Username: John Doe
Street name: Main St.
Street number: <script>alert('test')</alert>
Which of the following code snippets should the developer implement given the above transaction logs?
Question 25
The Chief information Officer (CIO) wants to establish a non-banding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a format partnership. Which of the follow would MOST likely be used?

