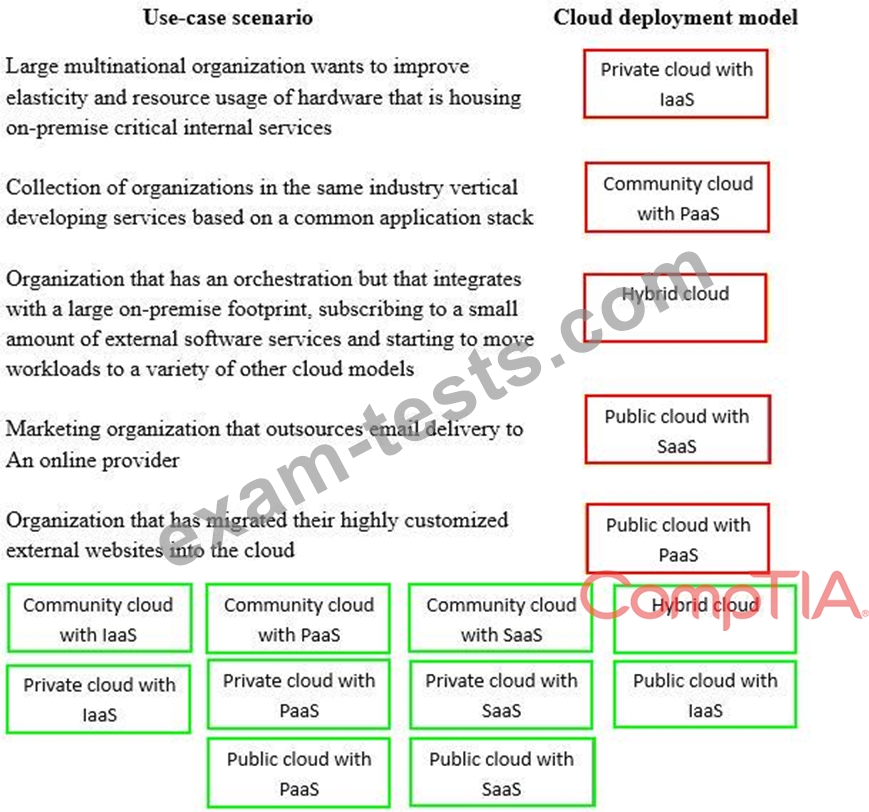
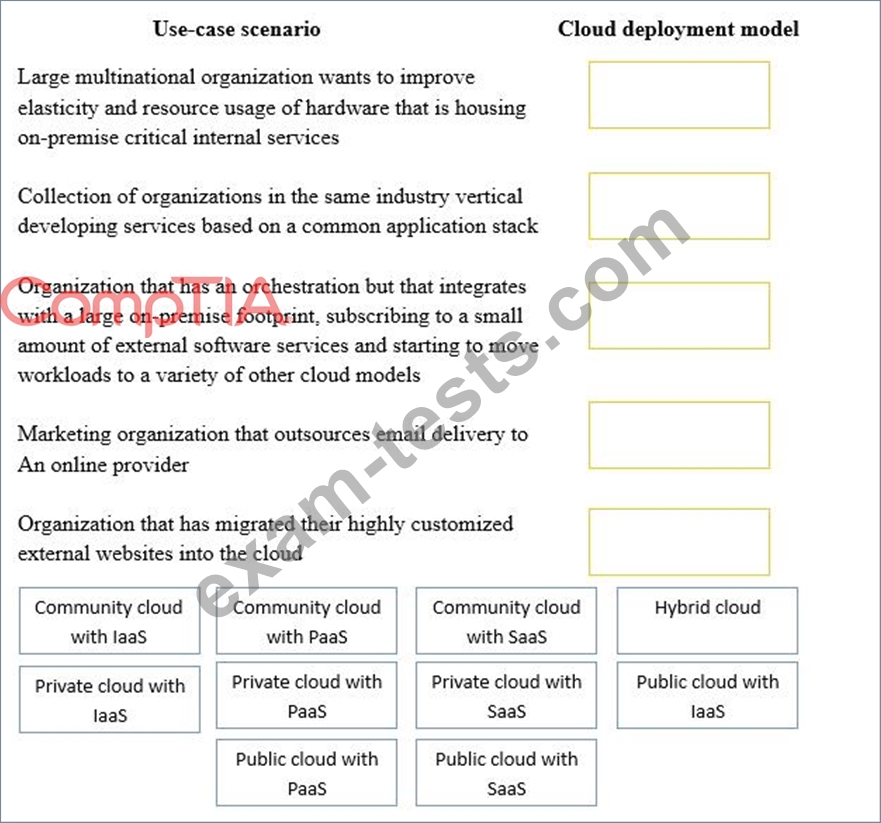
Question 381
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.

Question 382
A user has a laptop configured with multiple operating system installations. The operating systems are all installed on a single SSD, but each has its own partition and logical volume.
Which of the following is the BEST way to ensure confidentiality of individual operating system data?
Which of the following is the BEST way to ensure confidentiality of individual operating system data?
Question 383
A systems administrator receives an advisory email that a recently discovered exploit is being used in another country and the financial institutions have ceased operations while they find a way to respond to the attack. Which of the following BEST describes where the administrator should look to find information on the attack to determine if a response must be prepared for the systems? (Choose two.)
Question 384
Following a security assessment, the Chief Information Security Officer (CISO) is reviewing the results of the assessment and evaluating potential risk treatment strategies. As part of the CISO's evaluation, a judgment of potential impact based on the identified risk is performed. To prioritize response actions, the CISO uses past experience to take into account the exposure factor as well as the external accessibility of the weakness identified.
Which of the following is the CISO performing?
Which of the following is the CISO performing?
Question 385
Joe, a penetration tester, is assessing the security of an application binary provided to him by his client. Which of the following methods would be the MOST effective in reaching this objective?
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here: