Question 376
A security analyst is reviewing an endpoint that was found to have a rookit installed. The rootkit survived multiple attempts to clean the endpoints, as well as an attempt to reinstall the QS. The security analyst needs to implement a method to prevent other endpoint from having similar issues. Which of the following would BEST accomplish this objective?
Question 377
ABC Corporation has introduced token-based authentication to system administrators due to the risk of password compromise. The tokens have a set of HMAC counter-based codes and are valid until they are used. Which of the following types of authentication mechanisms does this statement describe?
Question 378
Aninternal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live.
The web host administrator collectsthe log files below and gives them to the development team so improvements can be made to the security design of the website.
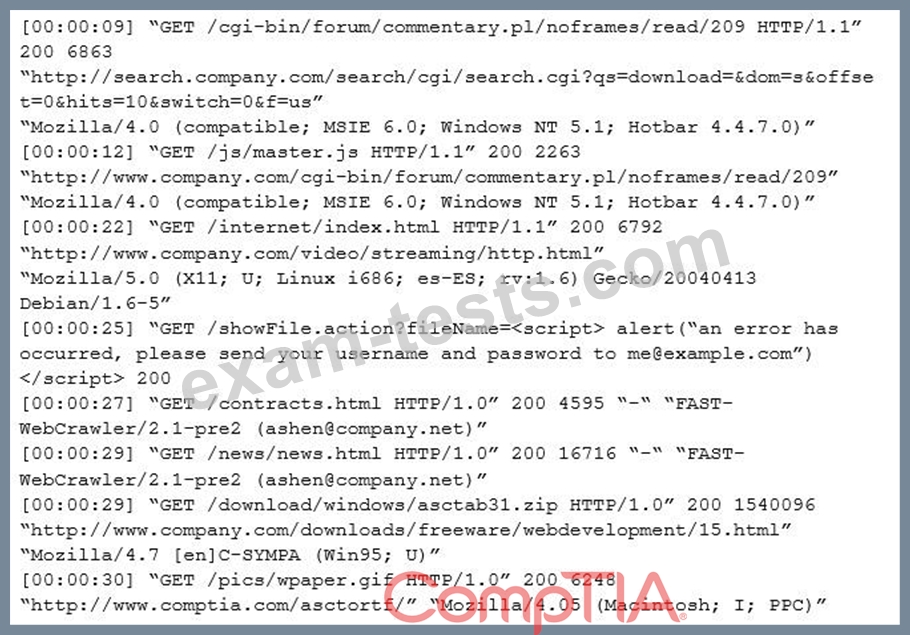
Which of the following types of attack vector did the penetration tester use?
The web host administrator collectsthe log files below and gives them to the development team so improvements can be made to the security design of the website.

Which of the following types of attack vector did the penetration tester use?
Question 379
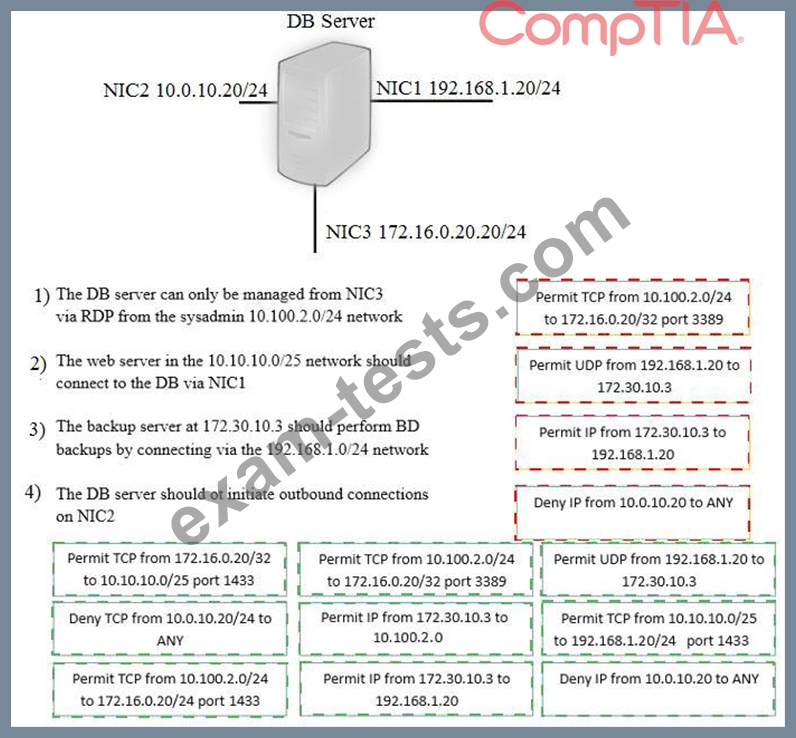
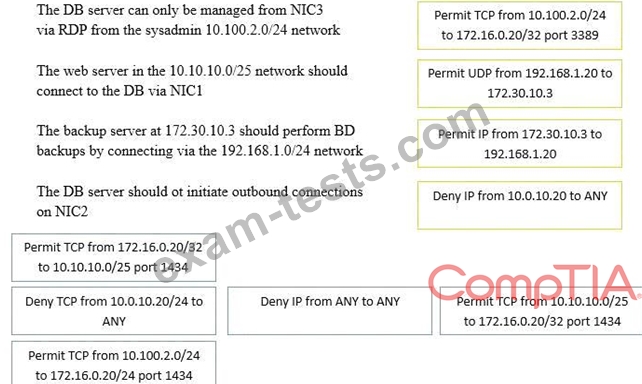
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.
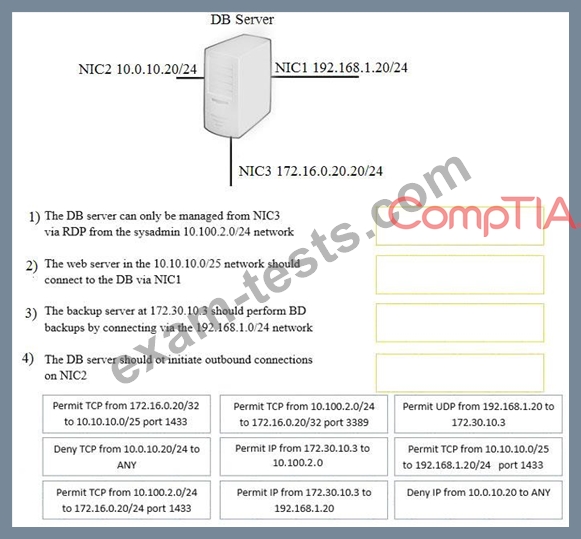

Question 380
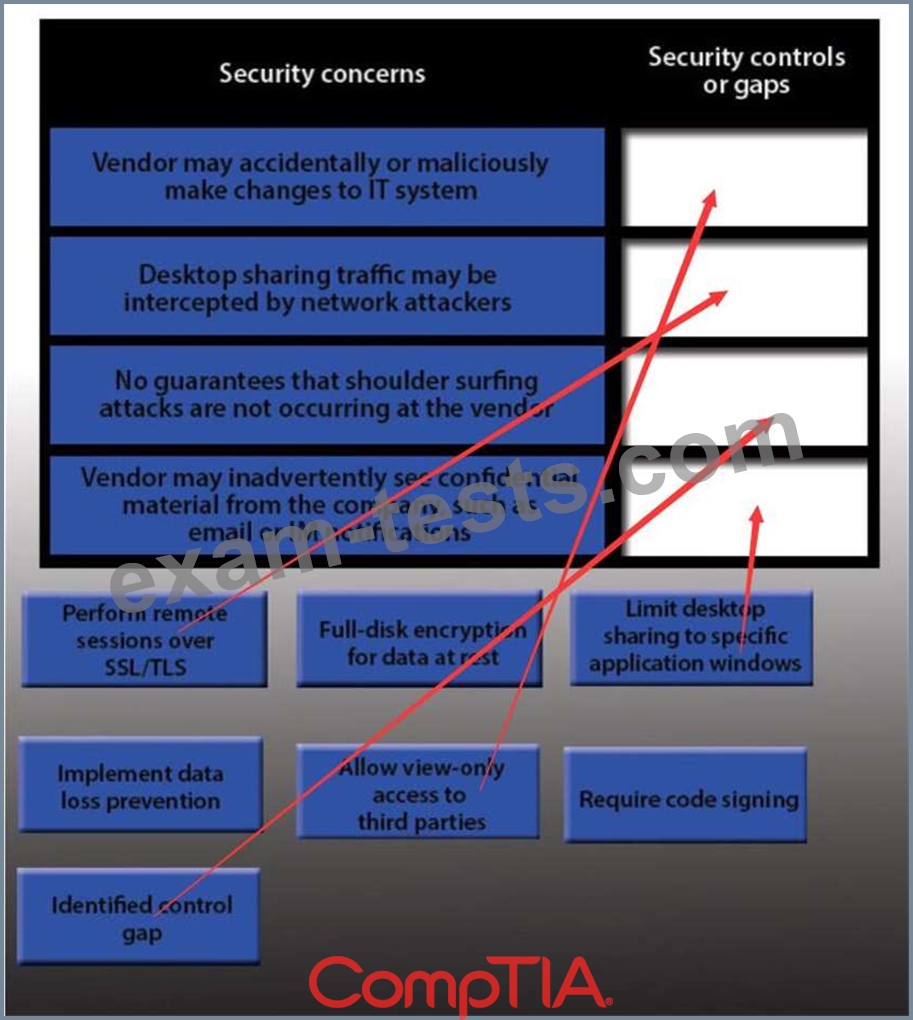
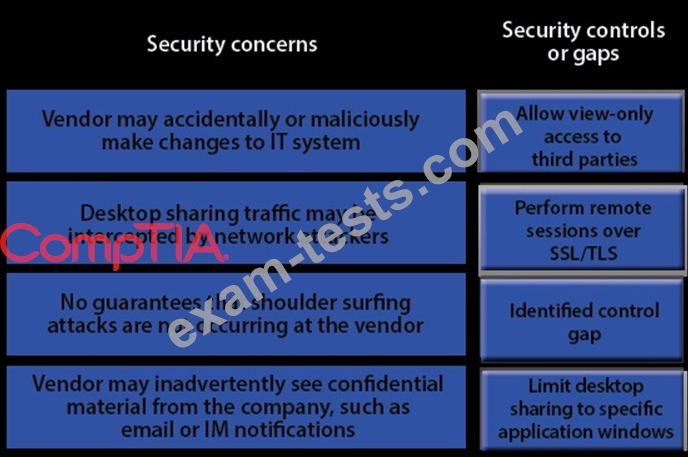
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern.
Options may be used once or not at all.
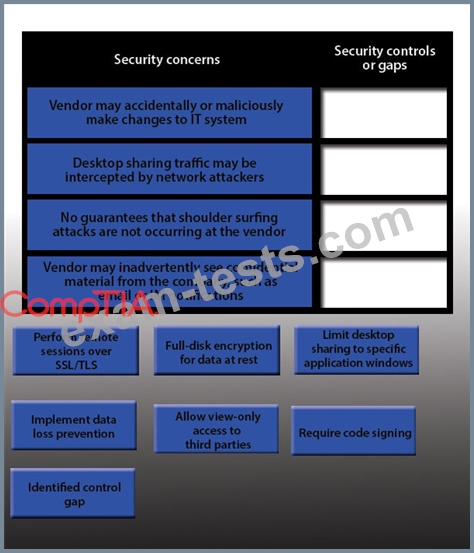
Options may be used once or not at all.