Question 371
A small retail company recently deployed a new point of sale (POS) system to all 67 stores. The core of the POS is an extranet site, accessible only from retail stores and the corporate office over a split-tunnel VPN. An additional split-tunnel VPN provides bi-directional connectivity back to the main office, which provides voice connectivity for store VoIP phones. Each store offers guest wireless functionality, as well as employee wireless. Only the staff wireless network has access to the POS VPN. Recently, stores are reporting poor response times when accessing the POS application from store computers as well as degraded voice quality when making phone calls.
Upon investigation, it is determined that three store PCs are hosting malware, which is generating excessive network traffic. After malware removal, the information security department is asked to review the configuration and suggest changes to prevent this from happening again. Which of the following denotes the BEST way to mitigate future malware risk?
Upon investigation, it is determined that three store PCs are hosting malware, which is generating excessive network traffic. After malware removal, the information security department is asked to review the configuration and suggest changes to prevent this from happening again. Which of the following denotes the BEST way to mitigate future malware risk?
Question 372
A Chief Information Securiy Officer (CISO) is reviewing technical documentation from various regional offices and notices some key differences between these groups. The CISO has not discovered any governance documentation. The CISO creates the following chart to visualize the differences among the networking used.
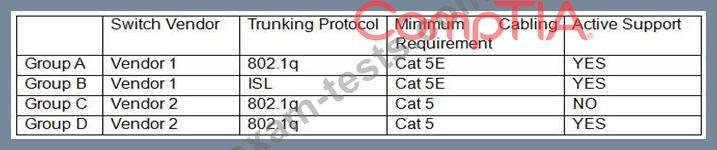
Which of the following would be the CISO's MOST immediate concern?

Which of the following would be the CISO's MOST immediate concern?
Question 373
A security administrator is assessing a new application. The application uses an API that is supposed to encrypt text strings that are stored in memory. How might the administrator test that the strings are indeed encrypted in memory?
Question 374
An analyst is investigating behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the "compose" window.
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
Question 375
The president of an online retail company has decided the company needs to increase its market size by targeting more countries in order to increase sales. All customer data is currently stored in the same country as the company's headquarters. Which of the following will be the GREATEST concern of the Chief Information Security Officer (CISO) when customers from foreign countries become customers?

