Question 406
An advanced threat emulation engineer is conducting testing against a client's network. The engineer conducts the testing in as realistic a manner as possible. Consequently, the engineer has been gradually ramping up the volume of attacks over a long period of time. Which of the following combinations of techniques would the engineer MOST likely use in this testing? (Choose three.)
Question 407
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below:
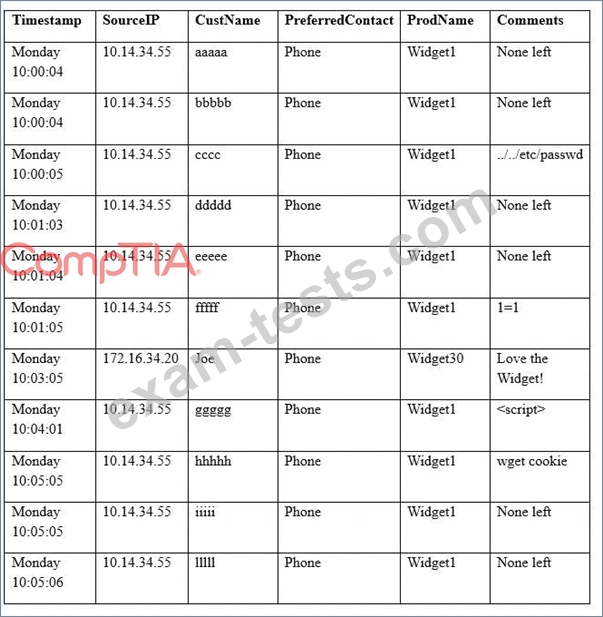
Which of the following is the MOST likely type of activity occurring?

Which of the following is the MOST likely type of activity occurring?
Question 408
A security administrator is updating a company's SCADA authentication system with a new application. To ensure interoperability between the legacy system and the new application, which of the following stakeholders should be involved in the configuration process before deployment? (Choose two.)
Question 409
First responders, who are part of a core incident response team, have been working to contain an outbreak of ransomware that also led to data loss in a rush to isolate the three hosts that were calling out to the NAS to encrypt whole directories, the hosts were shut down immediately without investigation and then isolated. Which of the following were missed? (Choose two.)
Question 410
An organization is reviewing endpoint security solutions. In evaluating products, the organization has the following requirements:
* Support server, laptop, and desktop infrastructure
* Due to limited security resources, implement active protection capabilities
* Provide users with the ability to self-service classify information and apply policies
* Protect data-at-rest and data-in-use
Which of the following endpoint capabilities would BEST meet the above requirements? (Select two.)
* Support server, laptop, and desktop infrastructure
* Due to limited security resources, implement active protection capabilities
* Provide users with the ability to self-service classify information and apply policies
* Protect data-at-rest and data-in-use
Which of the following endpoint capabilities would BEST meet the above requirements? (Select two.)

