Question 396
An SQL database is no longer accessible online due to a recent security breach. An investigation reveals
that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent
this type of breach in the future, which of the following security controls should be put in place before
bringing the database back online? (Choose two.)
that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent
this type of breach in the future, which of the following security controls should be put in place before
bringing the database back online? (Choose two.)
Question 397
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can view the outbound callback traffic, but sees no traffic between the two computers. Which of the following would BEST address the IDS visibility gap?
Question 398
When reviewing KRIs of the email security appliance with the Chief Information Security Officer (CISO) of an insurance company, the security engineer notices the following:
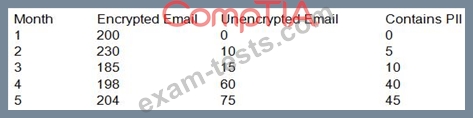
Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?

Which of the following measures should the security engineer take to ensure PII is not intercepted in transit while also preventing interruption to business?
Question 399
Ann, a retiring employee, cleaned out her desk. The next day, Ann's manager notices company equipment that was supposed to remain at her desk is now missing.
Which of the following would reduce the risk of this occurring in the future?
Which of the following would reduce the risk of this occurring in the future?
Question 400
A user asks a security practitioner for recommendations on securing a home network. The user recently
purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some
of the IoT devices are wearables, and other are installed in the user's automobiles. The current home
network is configured as a single flat network behind an ISP-supplied router. The router has a single IP
address, and the router performs NAT on incoming traffic to route it to individual devices.
Which of the following security controls would address the user's privacy concerns and provide the BEST
level of security for the home network?
purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some
of the IoT devices are wearables, and other are installed in the user's automobiles. The current home
network is configured as a single flat network behind an ISP-supplied router. The router has a single IP
address, and the router performs NAT on incoming traffic to route it to individual devices.
Which of the following security controls would address the user's privacy concerns and provide the BEST
level of security for the home network?

