Question 391
A security engineer is deploying an IdP to broker authentication between applications. These applications all utilize SAML 2.0 for authentication. Users log into the IdP with their credentials and are given a list of applications they may access. One of the application's authentications is not functional when a user initiates an authentication attempt from the IdP. The engineer modifies the configuration so users browse to the application first, which corrects the issue. Which of the following BEST describes the root cause?
Question 392
A recent assessment identified that several users' mobile devices are running outdated versions of endpoint security software that do not meet the company's security policy.
Which of the following should be performed to ensure the users can access the network and meet the company's security requirements?
Which of the following should be performed to ensure the users can access the network and meet the company's security requirements?
Question 393
Given the following code snippet:
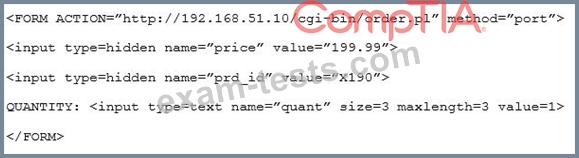
Of which of the following is this snippet an example?

Of which of the following is this snippet an example?
Question 394
A systems administrator recently joined an organization and has been asked to perform a security assessment of controls on the organization's file servers, which contain client data from a number of sensitive systems. The administrator needs to compare documented access requirements to the access implemented within the file system.
Which of the following is MOST likely to be reviewed during the assessment? (Choose two.)
Which of the following is MOST likely to be reviewed during the assessment? (Choose two.)
Question 395
An external penetration tester compromised one of the client organization's authentication servers and retrieved the password database. Which of the following methods allows the penetration tester to MOST efficiently use any obtained administrative credentials on the client organization's other systems, without impacting the integrity of any of the systems?
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

